At this time Woo’s engineering group deployed an vital replace for WooCommerce. The replace addresses a vulnerability that would permit unhealthy actors to inject malicious content material within the browser. The Woo group has additionally contacted WooCommerce retailers whose shops could also be weak.
This concern was restricted to WooCommerce shops working the following WooCommerce variations that additionally had Order Attribute enabled, a characteristic that’s enabled by default in WooCommerce:
| 8.8.0 | 8.8.1 | 8.8.2 | 8.8.3 |
| 8.8.4 | 8.9.0 | 8.9.1 | 8.9.2 |
If you’re working WooCommerce 8.8.0 or later, we strongly suggest updating as quickly as doable.
Actions it’s best to take to make sure your retailer is up to date
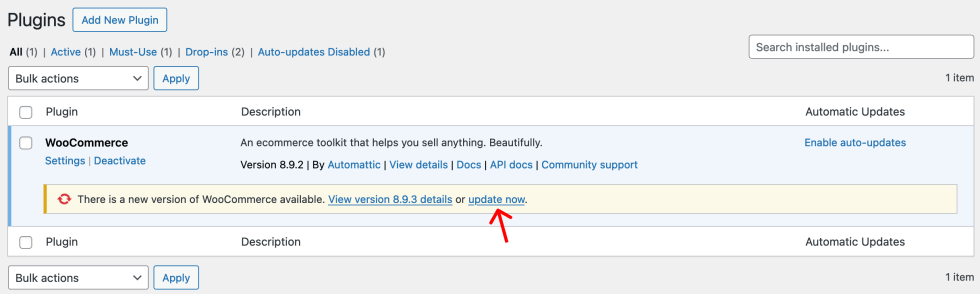
In the event you don’t have the suitable model put in already, you’ll have to replace it manually.
To replace the extension:
- Log in to your retailer’s WP Admin dashboard and navigate to Plugins.
- Find WooCommerce in your listing of put in plugins and extensions. You need to see an alert stating, “There’s a new model of WooCommerce accessible.”
- Click on the replace now hyperlink displayed on this alert to replace to model 8.9.3.
If you’re unable to replace WooCommerce instantly, it’s best to disable Order Attribution. This vulnerability is barely exploitable if Order Attribution is enabled.
You may learn extra in regards to the replace on this Woo Developer Advisory, together with tips on how to test your retailer’s model standing.
What’s the vulnerability?
This vulnerability might permit for cross-site scripting, a kind of assault wherein a foul actor manipulates a hyperlink to incorporate malicious content material (through code similar to JavaScript) on a web page. This might have an effect on anybody who clicks on the hyperlink, together with a buyer, the service provider, or a retailer admin.
Has my retailer’s information been compromised?
We’re not conscious of any exploits of this vulnerability. The difficulty was initially discovered by Automattic’s proactive safety analysis program with HackerOne. Our assist groups have acquired no reviews of it being exploited and our engineering group analyses didn’t reveal it had been exploited.
I take advantage of a model of WooCommerce older than 8.8.0; is my retailer impacted?
The vulnerability impacts any WooCommerce Store working WooCommerce 8.8.0, 8.8.1, 8.8.2, 8.8.3, 8.8.4, 8.9.0, 8.9.1, 8.9.2, particularly if the shop has Order Attribution enabled (that is enabled by default). If you’re utilizing an earlier secure, up to date model of WooCommerce, your retailer just isn’t affected.
How do I do know if my retailer is secure?
In case your retailer is working the newest, patched model of WooCommerce (8.9.3), it’s secure.
What else can I do to maintain my retailer safe?
We all the time encourage retailers to take care of excessive safety requirements. This contains using robust passwords, two-factor authentication, cautious monitoring of transactions, and utilizing the most recent, safe model of WooCommerce (and some other extensions or plugins put in in your website). Learn extra about safety greatest practices.
If in case you have additional considerations or questions, our group of Happiness Engineers is readily available to assist — please open a assist ticket.
Particular Thanks
We’re grateful for the assistance of safety researcher ecaron, who labored with us to uncover this vulnerability as a part of Automattic’s HackerOne Bounty Program.
