Embedded system designs all have one factor in frequent: a microprocessor and controller. These might be as sparse as 4-bit large controllers with lower than 1K of code house or as huge as a multicore multi-GHz processing supercomputer with Gis of code house. However, trendy IoT-based embedded system designs even have one other typical requirement. Many designs might be combined alerts, so virtually each design will embrace wi-fi communications.
Herein lies a problem. Will a designer select an overkill all-in open processor with way more efficiency, peripherals, reminiscence, and processing energy than is required simply to have a single built-in processor or devoted practical processors to deal with devoted and particular duties?
Each approaches might have advantage relying on a wide range of design constraints. Is time to market the driving drive? Is price the important constraint? What about measurement or energy effectivity? There are lots of components and microcontrollers/microprocessors to select from, particularly as embedded methods invade our dwelling house and develop into extra prevalent. Practically each place is now an clever setting.
Wi-fi Protocols
Each wi-fi machine makes use of some type of protocol to ascertain and keep communications. Whereas higher-cost, higher-end mobile protocols can be utilized for house and constructing communications, this carries the price of a recurring month-to-month mobile payment. Fashionable 4G and 5G methods fall into this class, using a variety of wi-fi protocols for enhanced connectivity.
Wi-Fi® is in style for media-based streaming and high-speed connectivity inside a facility. Many Wi-Fi ICs and modules are available for designers of their embedded design. Nonetheless, many designs don’t require the multi-Gbit/sec knowledge charges or have larger energy budgets to justify the extra subtle and expensive Wi-Fi medium.
Zigbee, Bluetooth®, and LTE are the extra power-friendly wi-fi protocols for room or constructing use. These require a lot much less firmware, reminiscence, and present, making them appropriate for distant controls, lighting methods, media methods, temperature sensors, smoke/fireplace detectors, heating/cooling methods, and extra.
What makes these protocols much more fascinating is the topological flexibility they provide. Along with point-to-point, these protocols can supply star, mesh, peer-to-peer, and client-server architectures. Star networks require every node to be in nearer proximity to the star heart, which is normally an aggregator. Peer-to-peer and mesh networks can “cross the baton” from node to node and canopy longer distances since packets propagate alongside a routing path. This may additionally assist protect battery life since not numerous transmission energy is required. Finally, packets which might be mandatory for connecting to the World Broad Internet will should be routed to an entry level. In all instances, safety needs to be used.
Safety
Typically, a safety breach might be simply an annoyance, like if somebody hacks into your good TV and modifications channels. Different instances might be extra critical, although, resembling somebody hacking into a house medical system. Dealing with these threats might be tackled in just a few methods, however the commonest technique is encryption.
Many encryption algorithms and requirements exist—some easy and a few very complicated. Wi-fi protocols like Zigbee and BLE have varied strategies of offering encryption safety. ZigBee makes use of 128-bit AES keys and is efficient at functions layers in addition to MAC layers. Bluetooth Low Power (BLE) permits 4 layers of safety:
- Stage 1: No Safety
- Used for eventualities the place knowledge confidentiality shouldn’t be a priority.
- Stage 2: Unauthenticated Pairing with Encryption
- Primary degree of safety, encrypting knowledge transmission with out verifying the identification of the connecting machine.
- Stage 3: Authenticated Pairing with Encryption
- Enhances safety with a way of authentication, resembling a PIN, earlier than establishing an encrypted connection.
- Stage 4: Authenticated LE Safe Connections
- The best degree of safety in BLE, which makes use of a sophisticated encryption algorithm for authenticated pairing and safe connections.
{Hardware}-accelerated safety capabilities can offload safety capabilities from firmware and make processors way more fascinating. {Hardware} encryption, decryption, hash code era, pseudo-random sequence turbines, and different blocks function at lightning velocity in {hardware} however take longer to implement in software program. This provides latency time and requires the programmer to generate and debug extra code.
Along with runtime knowledge safety, one other layer of safety must be in place, which is known as a safe boot. With safe boot, boot loader firmware is protected and locked, stopping anybody from rewriting this important code and redirecting its performance. Usually, unprotected firmware feeds a processor when it boots. Whether it is changed in flash one way or the other, the system is compromised. Safe boot takes benefit of strongly encrypted preliminary boot directions, which then use digital signatures to authenticate the subsequent layer of startup code.
A Dream Come True
Realizing the tightrope that designers need to stroll when selecting a perfect microcontroller/microprocessor, many machine makers are offering microcontrollers/microprocessors focusing on this huge marketplace for IoT, constructing automation, automotive, and industrial management. These functions want greater than a easy processor however don’t want an excellent processor. Whereas growth time must be fast, price and measurement are usually excessive on the record of constraints.
Top-of-the-line methods to get the processors and peripherals you want is to make use of a system-on-chip (SoC) answer. These modular models might be made by an OEM for small amount runs or used to prototype your individual larger quantity customized model.
The secret is the 64MHz PIC32CX-BZ3 household of processors based mostly on the 32-bit Cortex MF4 Arm. This processor brings a large number of peripherals and its safe boot ROM checks integrity and authenticity earlier than executing to make sure system root belief. There are additionally eight protected reminiscence zones and a ultimate fuse that makes it impenetrable.
The WBZ351 (Determine 1) drives the WBZ35x modules, which characteristic a totally compliant Bluetooth Low Power 5.2 transceiver. The transceiver can be Zigbee 3.0 licensed with software program stacks constructed across the sturdy MPLAB Concord v3 framework.
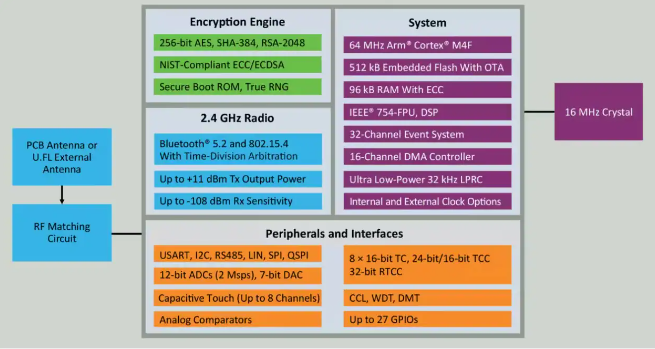
Additionally vital are the hardware-based safety accelerator and public important {hardware} (Determine 2). The AES safety encryption and HASH code generator are additionally included to create a safe execution setting. Anti-rollback and firmware readable life cycle encounters supply much more ranges of safety.
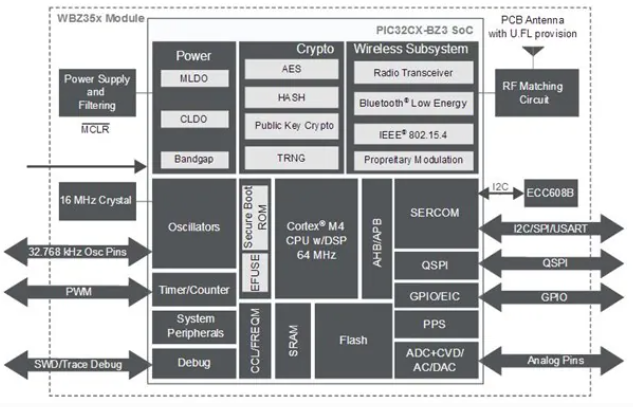
Conclusion
In the case of the IoT and good environments, designers have an enormous job. They have to combine wi-fi connectivity with strict safety measures. That’s the place Bluetooth Low Power and Zigbee are available in. These options can cowl massive areas with mesh networks whereas consuming much less energy. By incorporating safe boot and capacitive contact functionalities, designers can speed up concept-to-market and permit designers to satisfy the calls for for safety and consumer interplay in at this time’s IoT gadgets.
The PIC32CX-BZ3 household of processors packs all the pieces wanted into one place, together with superior connectivity choices and hardware-based safety features. By leveraging highly effective options, designers can navigate complicated trendy IoT ecosystems to make sure good environments are clever, safe, and user-friendly.

