
Throughout an evaluation of assorted splinter samples of a noteworthy macOS stealer, safety researchers at Moonlock found one with an alarming stage of sophistication. Underneath the disguise of the unreleased online game GTA6, as soon as put in, the malware executes reasonably intelligent strategies to extract delicate info, corresponding to passwords from a consumer’s native Keychain.
In typical Safety Chew vogue, right here’s the breakdown: the way it works and keep protected.
9to5Mac Safety Chew is solely delivered to you by Mosyle, the one Apple Unified Platform. Making Apple gadgets work-ready and enterprise-safe is all we do. Our distinctive built-in method to administration and safety combines state-of-the-art Apple-specific safety options for absolutely automated Hardening & Compliance, Subsequent Era EDR, AI-powered Zero Belief, and unique Privilege Administration with probably the most highly effective and trendy Apple MDM available on the market. The result’s a very automated Apple Unified Platform at present trusted by over 45,000 organizations to make thousands and thousands of Apple gadgets work-ready with no effort and at an inexpensive value. Request your EXTENDED TRIAL right now and perceive why Mosyle is all the things you could work with Apple.

As I reported in a earlier version of Safety Chew, malware specifically made to focus on macOS continues to germinate in recognition as Mac grows in recognition. Final yr, 21 new malware households have been found within the wild, up 50% from 2022.
Regardless of this reality, there nonetheless exists a typical false impression that menace actors don’t goal Apple machines. Whereas this will have been true previously, it’s definitely not the case right now. Not solely is the variety of malware assaults rising, however they’re additionally changing into extra refined than ever.
The way it works
Throughout evaluation, Moonlock, the cybersecurity division of MacPaw, discovered the brand new malware pattern is a variant of password-stealing ware (PSW), a kind of trojan malware designed to gather logins and passwords from contaminated machines and ship them again to the menace actor through a distant connection or e mail.
Researchers discovered the malware disguises itself as a duplicate of GTA6 or a pirated model of Notion. It is a widespread social engineering trick that exploits belief by utilizing acquainted nomenclature to deceive customers into downloading malware.
Notably, all Macs include a model of macOS Gatekeeper put in that works within the background to forestall customers from downloading unsigned functions from the Web that might comprise malware. A consumer, nevertheless, can override this safety characteristic by merely right-clicking on the DMG file and hitting “Open.” Cybercriminals exploit this ease by together with a graphic instructing the consumer on open the malicious file.
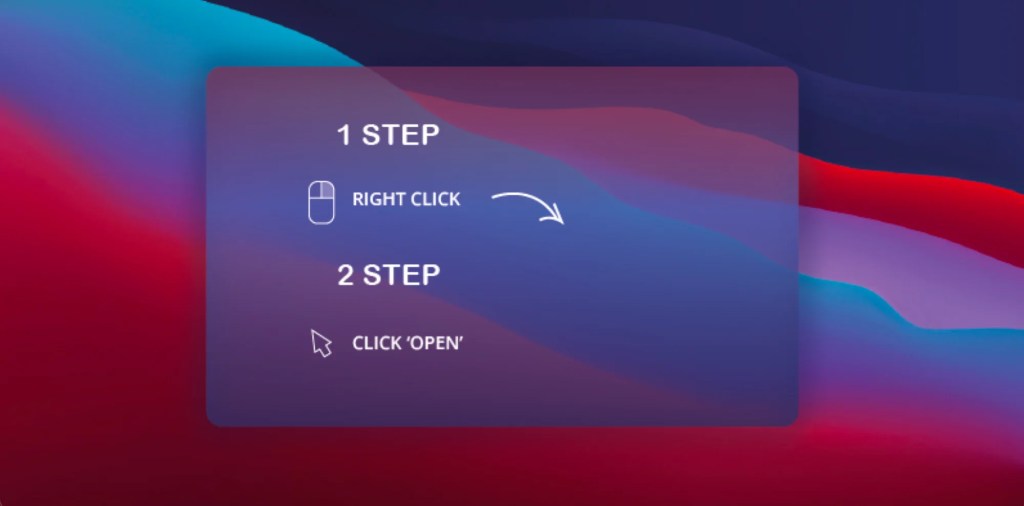
Upon execution, the DMG unleashes a Mach-O file named AppleApp.
“Subsequently, AppleApp initiates a GET request to a selected URL originating from a Russian IP deal with. If the connection is profitable, this system will start to obtain {a partially} obfuscated AppleScript and Bash payload. This payload is instantly executed from utility reminiscence, bypassing the file system,” Moonlock acknowledged in a weblog put up in regards to the findings.
When executed, the payload makes use of a multi-faceted method to realize its malicious goals. On this order:
- Phishing for credentials
- Focusing on delicate information
- System profiling
- Information exfiltration
Since a neighborhood Keychain database is accessible solely with a consumer’s system password, the malware performs its second intelligent method. It deploys a pretend helper app set up window, additional exploiting belief and tricking the consumer into revealing their password.
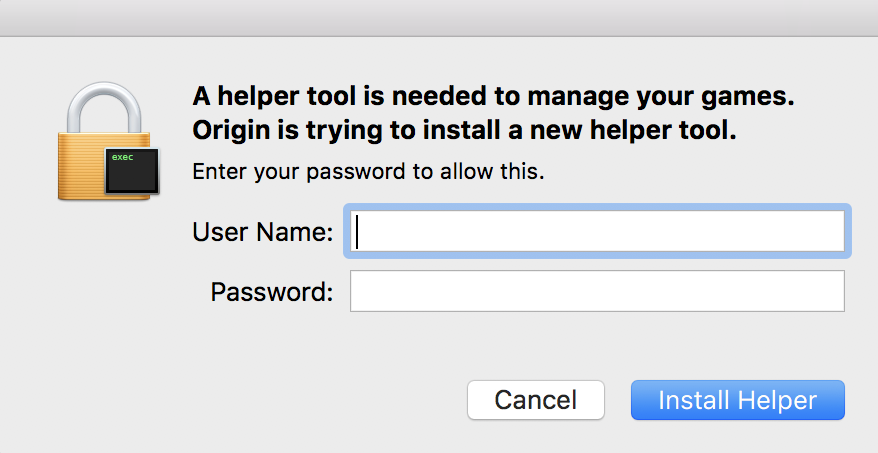
The malware now begins to focus on Keychain databases and lots of different sources of delicate information.
“With precision, the malware hunts by system directories, on the lookout for precious information corresponding to cookies, kind historical past, and login credentials from fashionable internet browsers together with Chrome, Firefox, Courageous, Edge, Opera, and OperaGX. Moreover, it seeks the latest servers record from FileZilla, macOS Keychain databases, and the wallets of cryptocurrencies.”
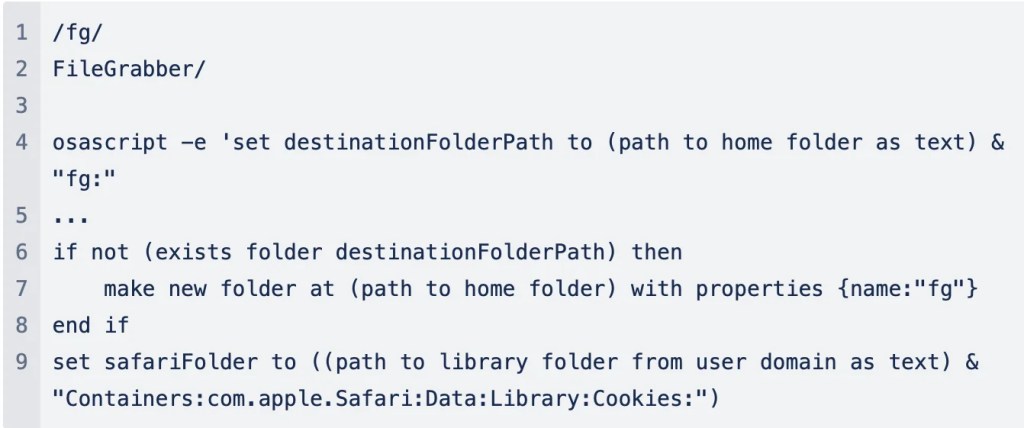
Furthermore, utilizing extra refined AppleScripts, the malware establishes a secret folder inside customers’ residence directories. Right here, any collected logins, passwords, and keys are saved to await extraction from the contaminated system to an exterior server managed by the cybercriminal.
Easy methods to keep protected from macOS stealers
Whereas solely about 6% of all malware targets Mac customers, menace actors are actively concentrating on macOS extra now than ever. It’s essential to remain vigilant and proceed to make use of widespread Web smarts.
When you could already know lots of the following pointers, I feel it’s essential to regurgitate them once more in relation to macOS stealers:
- Do your due diligence earlier than putting in something outdoors the official Mac App Retailer
- Underneath no circumstance ought to a consumer observe directions to bypass Gatekeeper
- Train warning with any system prompts or requests for delicate info
- Preserve your gadgets and functions up-to-date to guard towards the newest threats and vulnerabilities
Extra in safety
FTC: We use earnings incomes auto affiliate hyperlinks. Extra.
