Ransomware actors are once more utilizing TeamViewer to realize preliminary entry to group endpoints and try and deploy encryptors primarily based on the leaked LockBit ransomware builder.
TeamViewer is a official distant entry software used extensively within the enterprise world, valued for its simplicity and capabilities.
Sadly, the software can also be cherished by scammers and even ransomware actors, who use it to realize entry to distant desktops, dropping and executing malicious information unhindered.
An identical case was first reported in March 2016, when quite a few victims confirmed within the BleepingComputer boards that their gadgets have been breached utilizing TeamViewer to encrypt information with the Shock ransomware.
On the time, TeamViewer’s clarification for the unauthorized entry was credential stuffing, that means the attackers didn’t exploit a zero-day vulnerability within the software program however as an alternative used customers’ leaked credentials.
“As TeamViewer is a broadly unfold software program, many on-line criminals try to go browsing with the info of compromised accounts, so as to discover out whether or not there’s a corresponding TeamViewer account with the identical credentials,” defined the software program vendor on the time.
“If that is so, chances are high they’ll entry all assigned gadgets, so as to set up malware or ransomware.”
TeamViewer focused once more
A brand new report from Huntress exhibits that cybercriminals have not deserted these outdated strategies, nonetheless taking up gadgets by way of TeamViewer to try to deploy ransomware.
The analyzed log information (connections_incoming.txt) confirmed connections from the identical supply in each circumstances, indicating a standard attacker.
Within the first compromised endpoint, Huntress noticed within the logs a number of accesses by staff, indicating the software program was actively utilized by the workers for official administrative duties.
Within the second endpoint seen by Huntress, which has been operating since 2018, there had been no exercise within the logs for the previous three months, indicating that it was much less ceaselessly monitored, presumably making it extra engaging for the attackers.
In each circumstances, the attackers tried to deploy the ransomware payload utilizing a DOS batch file (PP.bat) positioned on the desktop, which executed a DLL file (payload) by way of a rundll32.exe command.
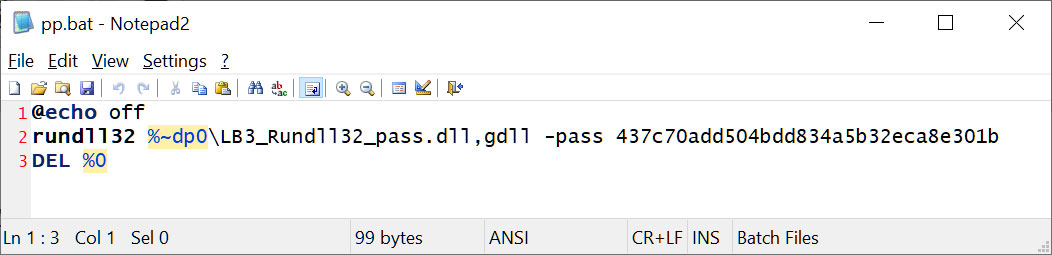
Supply: BleepingComputer
The assault on the primary endpoint succeeded however was contained. On the second, the antivirus product stopped the trouble, forcing repeated payload execution makes an attempt with no success.
Whereas Huntress hasn’t been capable of attribute the assaults with certainty to any recognized ransomware gangs, they word that it’s much like LockBit encryptors created utilizing a leaked LockBit Black builder.
In 2022, the ransomware builder for LockBit 3.0 was leaked, with the Bl00dy and Buhti gangs rapidly launching their very own campaigns utilizing the builder.
The leaked builder means that you can create completely different variations of the encryptor, together with an executable, a DLL, and an encrypted DLL that requires a password to launch correctly.
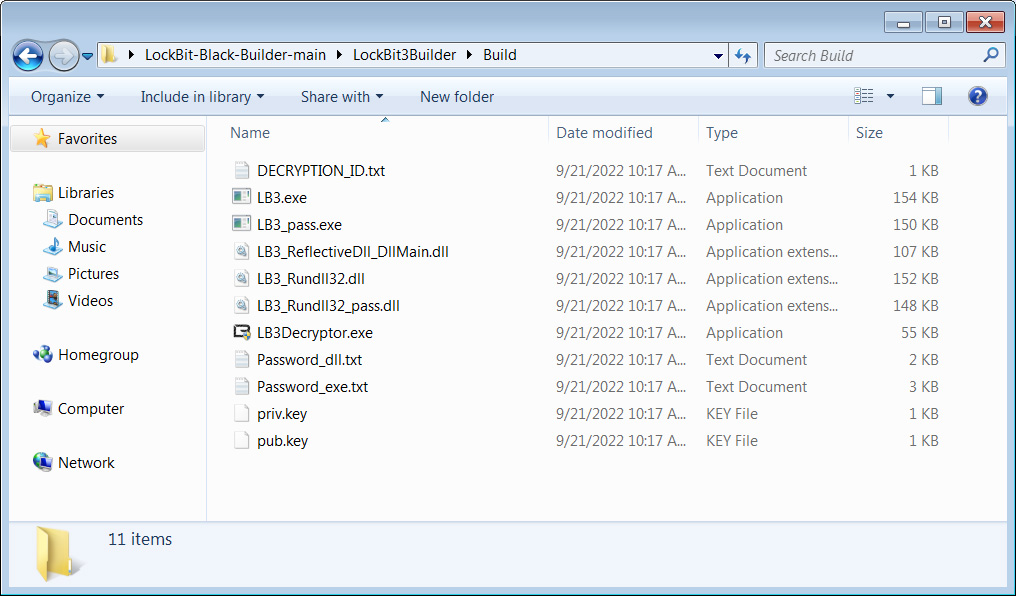
Supply: BleepingComputer
Primarily based on the IOCs supplied by Huntress, the assaults via TeamViewer seem like utilizing the password-protected LockBit 3 DLL.
Whereas BleepingComputer couldn’t discover the precise pattern seen by Huntress, we discovered a completely different pattern uploaded to VirusTotal final week.
This pattern is detected as LockBit Black however doesn’t use the usual LockBit 3.0 ransomware word, indicating it was created by one other ransomware gang utilizing the leaked builder.
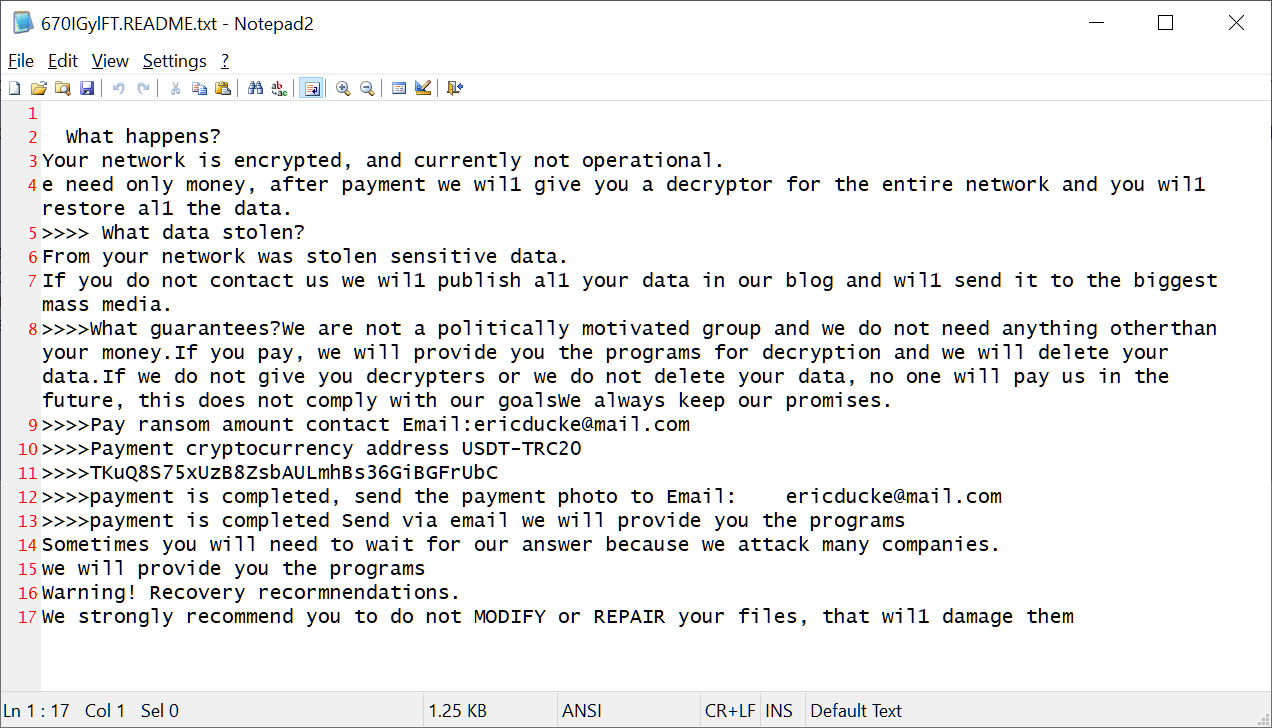
Supply: BleepingComputer
Whereas it’s unclear how the menace actors at the moment are taking management of TeamViewer situations, the corporate shared the next assertion with BleepingComputer in regards to the assaults and on securing installations.
“At TeamViewer, we take the safety and integrity of our platform extraordinarily severely and unequivocally condemn any type of malicious use of our software program.
Our evaluation exhibits that almost all situations of unauthorized entry contain a weakening of TeamViewer’s default safety settings. This typically contains the usage of simply guessable passwords which is simply attainable by utilizing an outdated model of our product. We continuously emphasize the significance of sustaining robust safety practices, corresponding to utilizing complicated passwords, two-factor-authentication, allow-lists, and common updates to the newest software program variations. These steps are vital in safeguarding towards unauthorized entry.
To additional help our customers in sustaining safe operations, we have now revealed a set of greatest practices for safe unattended entry, which could be discovered at [Best practices for secure unattended access – TeamViewer Support]. We strongly encourage all our customers to comply with these tips to boost their safety posture.”
