
You not often root for a cybercriminal, however a brand new malware marketing campaign concentrating on baby exploiters would not make you are feeling dangerous for the victims.
Since 2012, menace actors have been creating a wide range of malware and ransomware that faux to be authorities businesses warning contaminated Home windows customers that they have been viewing CSAM. The malware tells victims they have to pay a “penalty” to forestall their data from being despatched to regulation enforcement.
One of many first “fashionable” ransomware operations, known as Anti-Youngster Porn Spam Safety or ACCDFISA, used this extortion tactic mixed with initially locking Home windows desktops and encrypting information in later variations.
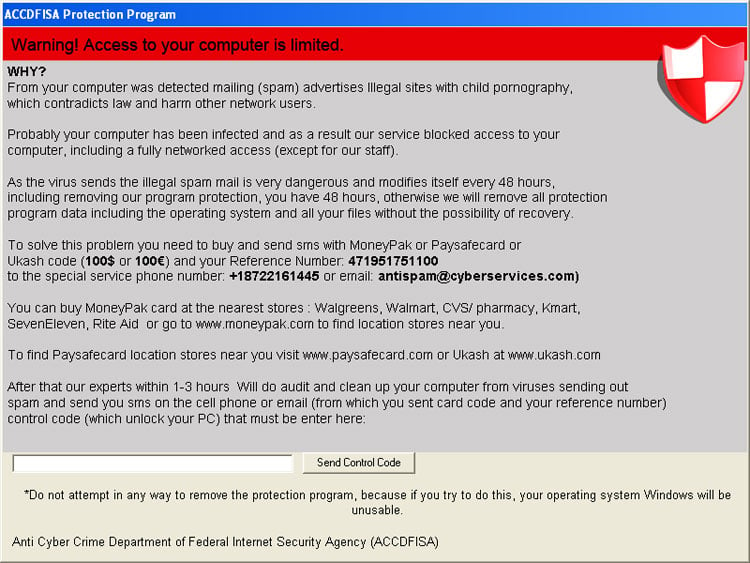
Supply: BleepingComputer
Quickly adopted different malware households that pretended to be regulation enforcement issuing fines for watching CSAM, corresponding to Harasom, Urausy, and the Reveton trojans.
An unlikely hero
Final week, cybersecurity researcher MalwareHunterTeam shared a pattern of a malware executable with BleepingComputer known as ‘CryptVPN’ [VirusTotal] utilizing related extortion techniques.
Nevertheless, this time, slightly than concentrating on harmless folks, the malware developer is concentrating on those that actively hunt down baby pornography.
After researching the malware, BleepingComputer discovered that menace actors created a web site to impersonate UsenetClub, a subscription service for “uncensored” entry to photographs and movies downloaded from Usenet.
Usenet is a web-based dialogue platform permitting folks to debate numerous subjects in “newsgroups” to which they subscribe. Whereas Usenet is used for legitimate dialogue on a variety of points, it is usually a recognized supply of kid pornography.
A faux website created by the menace actors pretends to be UsenetClub, providing three subscription tiers to the location’s content material. The primary two are paid-for subscriptions starting from $69.99 per 30 days to $279.99 per yr.
Nevertheless, a 3rd possibility claims to supply free entry after you put in a free “CryptVPN” software program and use it to entry the location.
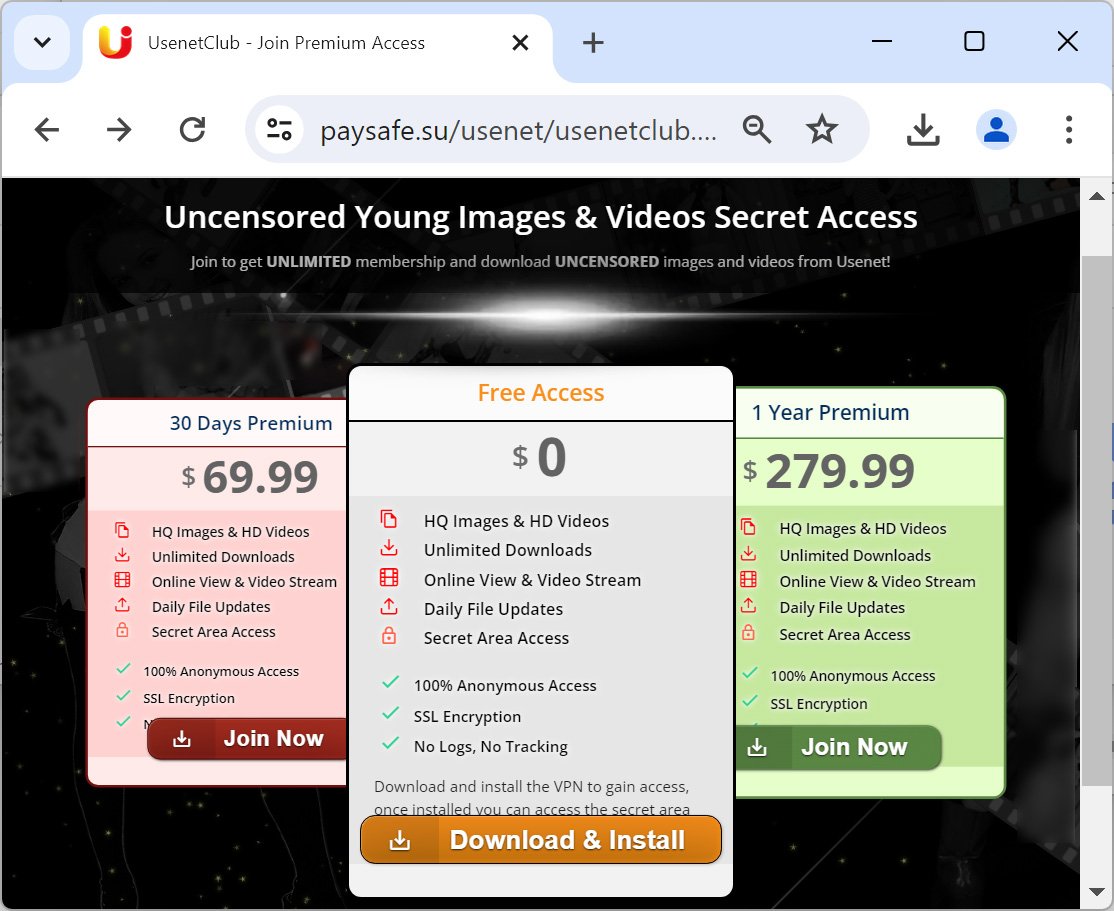
Supply: BleepingComputer
Clicking on the “Obtain & Set up” button will obtain a CryptVPN.zip file from the location that, when extracted, comprises a Home windows shortcut known as “CLICK-HERE-TO-INSTALL”.
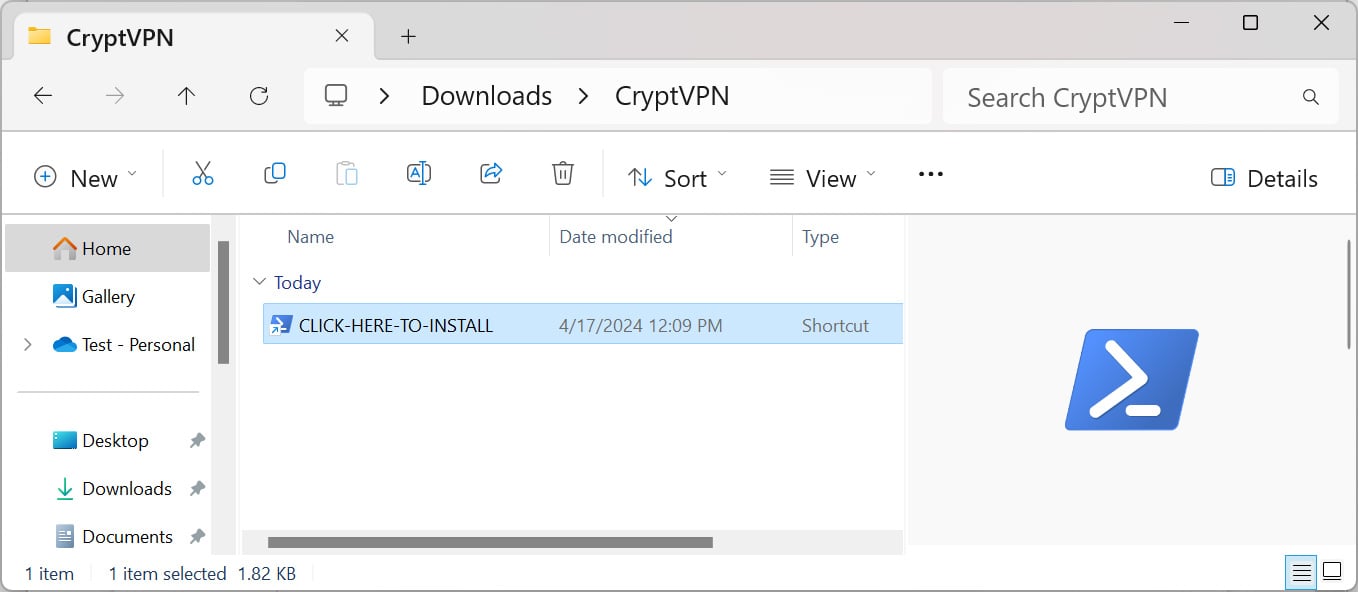
Supply: BleepingComputer
This file is a shortcut to the PowerShell.exe executable with arguments to obtain the CryptVPN.exe executable, reserve it to C:WindowsTasks.exe, and execute it.
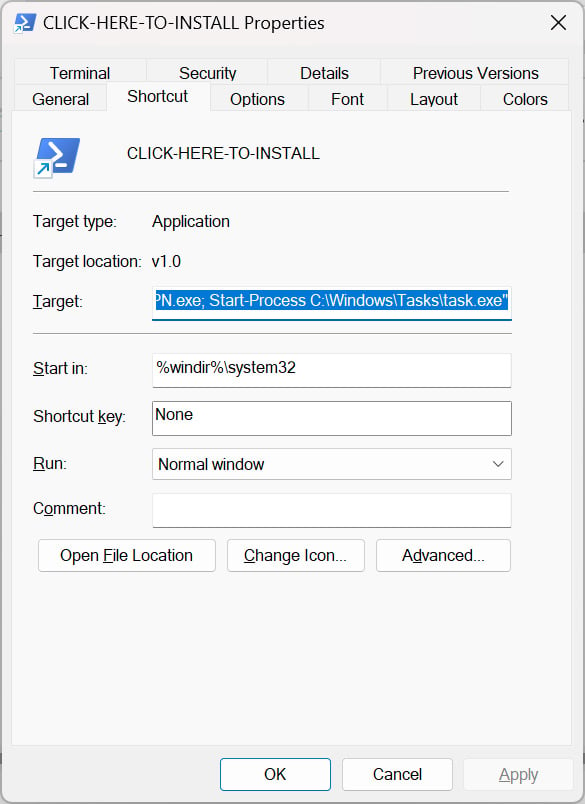
Supply: BleepingComputer
The malware executable is filled with UPX, however when unpacked, it comprises a PDB string that signifies that the writer known as the malware “PedoRansom”.
C:UsersusersourcereposPedoRansomx64ReleasePedoRansom.pdb
There’s nothing particular in regards to the malware as all it does is change the goal’s wallpaper to an extortion demand and drops a ransom be aware named README.TXT on the desktop, containing related extortion threats.
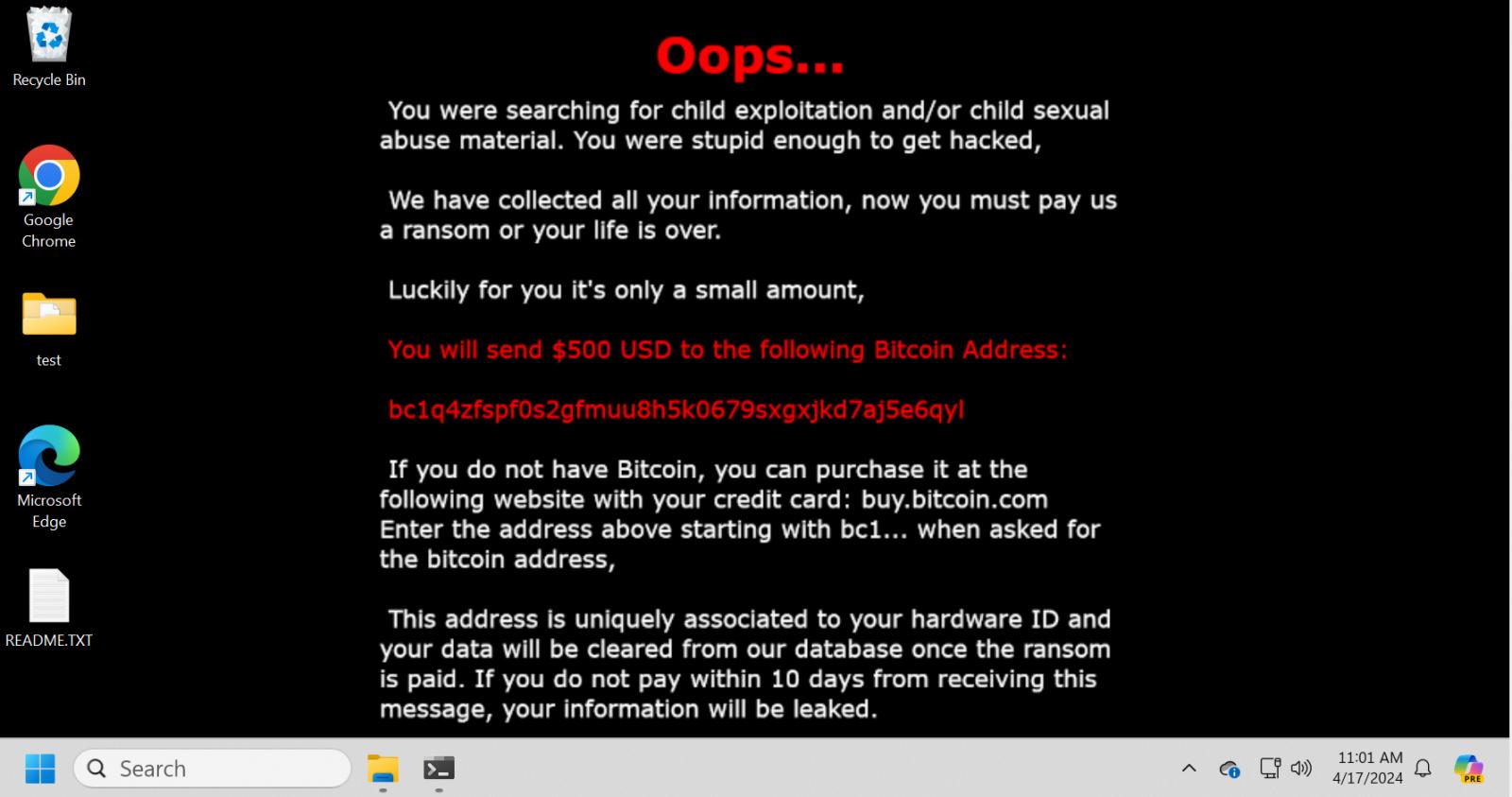
Supply: BleepingComputer
“You have been looking for baby exploitation and/or baby sexual abuse materials. You have been silly sufficient to get hacked,” reads the extortion demand.
“We’ve got collected all of your data, now you will need to pay us a ransom or your life is over.”
The extortion goes on to state that the individual should pay $500 to the bc1q4zfspf0s2gfmuu8h5k0679sxgxjkd7aj5e6qyl Bitcoin tackle inside ten days or their data will likely be leaked.
This bitcoin tackle has solely acquired roughly $86 in funds at the moment.
Risk actors have been utilizing “sextortion” techniques for a very long time, generally sending mass emails to massive numbers of individuals to try to scare them into paying an extortion demand.
These techniques carried out very nicely initially, with spammers extorting over $50,000 weekly within the early campaigns.
Nevertheless, as time has passed by and recipients of those scams have grown wiser, sextortion campaigns don’t generate the identical income as they as soon as did.
Whereas this specific marketing campaign is a little more ingenious and can scare many searching for any such content material, we’ll probably not see many individuals paying this extortion demand.
