Latest occasions, akin to these affecting SolarWinds and Log4j, show the dimensions of cybersecurity disruption that may end result from a scarcity of vigilance with regards to the administration of third-party parts in software program techniques. As techniques have develop into more and more software program intensive and complicated, these third-party parts have develop into widespread, they usually require an built-in acquisition, engineering, growth, and operational focus to make sure ample safety and resilience. Nonetheless, a latest report by SecurityScorecard examined greater than 230,000 organizations and located that the techniques of 98 p.c of them have had third-party software program parts breached throughout the previous two years.
In gentle of those realities, these charged with managing software program techniques should contemplate the dependencies and dangers of third-party software program in new methods and collaborate with enterprise consultants to develop new methods for figuring out and managing potential dangers. A software program invoice of supplies (SBOM) can facilitate these duties. This SEI Weblog put up highlights our work to construct on the SEI’s Acquisition Safety Framework for provide chain threat administration and tailor it to be used in third-party software program administration, which resulted within the SEI SBOM Framework.
Software program and Provide Chain Cybersecurity Challenges
Third-party threat is a serious problem for organizations looking for to restrict their publicity to cybersecurity dangers. As a result of third-party software program has develop into such an necessary issue within the safety of huge, advanced techniques, managing relationships with third-party distributors is vital for achievement.
Organizations usually have a restricted view into the parts, sources, and suppliers concerned in a system’s growth and ongoing operation. A necessary facet of addressing provider threat is having the ability to entry details about provider inputs and their relative significance, after which handle mitigations to cut back threat.
Nonetheless, a program can not successfully handle cybersecurity dangers alone, as a result of safety and provider threat administration usually lie outdoors this system’s scope. Furthermore, vital info mandatory for cyber threat administration is commonly distributed amongst many paperwork, akin to a program safety plan (PPP), cybersecurity plan, system growth plan (SDP), or provide chain threat administration plan. Likewise, many actions vital to managing cyber dangers are distributed amongst models all through the group. These models should collaboratively tackle cyber threat administration throughout the lifecycle and provide chain and combine this work with program threat administration (Determine 1).
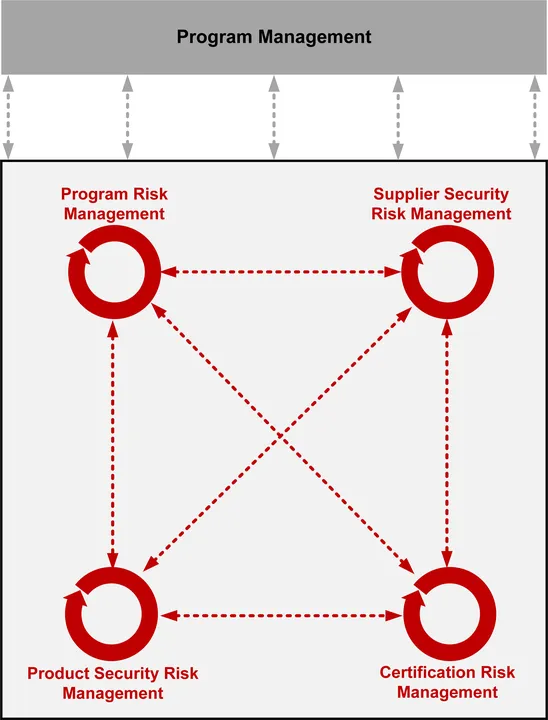
Determine 1: Managing Threat Requires an Built-in, Collaborative, Information-Pushed Method Throughout the Lifecycle and Provide Chain.
SBOMs and Alternatives for Their Use
The U.S. Division of Commerce (DOC) defines an SBOM as follows in its paper The Minimal Components for a Software program Invoice of Supplies (SBOM):
An SBOM is a proper report containing the main points and provide chain relationships of varied parts utilized in constructing software program.
Program mangers more and more depend on SBOM-driven methods for gathering details about the parts, and their sources or suppliers, that comprise software program techniques. Early efforts to innovate SBOM strategies centered on defining information components and managing identified vulnerabilities. In consequence, a number of info and threat administration strategies have emerged that establish vital information and join assist groups, suppliers, and stakeholders to cut back threat.
The SBOM gained added significance with Govt Order (EO) 14028, Enhancing the Nation’s Cybersecurity. Issued on Could 12, 2021, EO 14028 requires U.S. authorities companies to boost software program provide chain safety and integrity, with a precedence on addressing vital software program. s A key part to reaching software program provide chain safety and integrity is transparency, and SBOMs for vital software program may help set up this transparency within the software program provide chain. Because of this EO 14028 requires requirements, procedures, and standards for offering SBOMs for merchandise straight or publishing them on a public web site.
Our survey of SBOM publications and steering revealed a powerful emphasis on defining the content material and format of SBOMs. Whereas establishing a typical for SBOM content material is necessary, organizations additionally want steering on methods to plan for, develop, deploy, and use SBOMs. Consequently, we centered our analysis actions on the SBOM lifecycle (i.e., the set of actions required to plan for, develop, and use an SBOM). Nonetheless, SBOMs should additionally assist (1) proactively contemplating methods to greatest handle dangers posed by third events, and (2) growing efficient mitigations as new threats and vulnerabilities emerge.
There’s broad assist for growing the utility of SBOMs. A mandatory subsequent step is to develop main practices and supporting processes. Creating extra complete and collaborative SBOM apply frameworks will supply methods for successfully establishing and managing proactive software program info and threat administration packages. SBOMs can even present software program builders, integrators, and threat managers a singular alternative to gather info they’ll analyze, monitor, and act on to handle software program parts, suppliers, dependencies, provenance, vulnerabilities, and extra—the probabilities are limitless.
We additionally acknowledge that the SBOM lifecycle doesn’t exist in isolation. Slightly, it’s carried out in an organizational context. Along with the core lifecycle actions, we should contemplate enabling and supporting different actions, akin to these carried out by program administration, organizational assist (e.g., info expertise, threat administration, and alter administration), and third events. Going ahead, you will need to look creatively at how SBOM information can be utilized to handle software program threat and effectivity, and the way it can present assist to groups that may profit from collaborative efforts to unravel issues.
Constructing the SBOM Framework
We began growing the SBOM Framework by reviewing printed use circumstances. Based mostly on this evaluation, we developed core SBOM practices, which centered totally on growing SBOMs and utilizing them to handle identified safety vulnerabilities and related dangers. We then expanded on this preliminary set of practices by contemplating a lifecycle perspective, which recognized practices for specifying necessities, growing plans, and allocating assets wanted to construct and use SBOMs. Lastly, we recognized practices for actions that allow and assist operational use of SBOM information, together with administration and assist practices, third-party practices, and infrastructure practices. The result’s an SBOM Framework comprising the next targets (with third-party practices included within the Necessities and Handle/Help targets):
- Necessities
- Planning
- Constructing/Development
- Deployment/Use
- Administration/Help
Our SBOM framework gives a place to begin for integrating SBOMs with a program’s safety threat administration practices. As we gather classes discovered from piloting the framework and suggestions from the group, we are going to replace the framework’s targets and practices as acceptable.
Leveraging SBOM Data
SBOMs have been primarily designed to assist organizations construct extra construction into the administration of software program dangers. Administration practices should not solely establish, however successfully mitigate, safety and resilience dangers in techniques. Nonetheless, information and knowledge from SBOMs, whereas a key consider managing threat, has many different potential makes use of and improvements.
Reaching efficient SBOM outcomes requires planning, tooling to scale, assets educated to do the job, measurement, and/or monitoring. Data gathered from an SBOM can supply insights into the challenges confronted by the teams engaged in managing a system. Determine 2 presents a number of the assist groups that would use and profit from SBOM info and key questions this info can tackle to enhance software program and techniques.

Determine 2: Groups That Can Profit from SBOM Data.
Information about software program dangers and vulnerabilities is wealthy and in depth. Sadly, the chance info that SBOMs include solely provides to an already overwhelming move of knowledge. Organizing and prioritizing that info is a problem, however we anticipate the SBOM Framework to assist customers with these duties.
SBOM information evaluation can even assist visualize exhausting or, in some circumstances, unseen relationships and dependencies. These relationships and dependencies will be invaluable to groups who handle software program in ever extra advanced technical environments. That profit was described in The Minimal Components for a Software program Invoice of Supplies (SBOM):
An SBOM ought to include all major (prime stage) parts, with all their transitive dependencies listed. At a minimal, all top-level dependencies have to be listed with sufficient element to hunt out the transitive dependencies recursively.
Going additional into the graph will present extra info. As organizations start SBOM, depth past the first parts will not be simply obtainable because of present necessities with subcomponent suppliers. Eventual adoption of SBOM processes will allow entry to extra depth by means of deeper ranges of transparency on the subcomponent stage.
With this name for improved information visualization in thoughts, we supplemented our growth of the SEI SBOM Framework with a facet challenge geared toward graphing information exported from an SBOM instrument. We ingest the information to create the graphical prototypes for additional analysis and evaluation (in SDPX format, which is an open customary for speaking SBOM info).
A Framework for Increasing the Utility of SBOMs
SBOMs have gotten essential in managing software program and system threat and resilience. Motivated by EO 14028, a number of efforts are underway to develop their use. Extra importantly, there may be vast and rising recognition that the dangers posed by a scarcity of transparency in software program have to be addressed to assist guarantee safety and promote system resilience. We consider the practices and processes outlined in our SBOM Framework can present a place to begin to construction for SBOM efforts. This framework addresses the institution of processes to handle a number of SBOMs and the huge information that they’ll present; nonetheless, these processes will doubtless require additional tuning as pilot-related actions present enter about enhancements and tooling.
We hope our SBOM Framework will assist promote the usage of SBOMs and set up a extra complete set of practices and processes that organizations can leverage as they construct their packages. In the meantime, we are going to proceed speaking broadly about the advantages and potential makes use of of SBOMs and collect suggestions from pilots. We may even proceed to discover pilot alternatives. The place adoption of the SBOM Framework has occurred, we are going to research the teachings discovered to assist us in making refinements.
For a extra complete dialogue of the SEI SBOM Framework, we encourage you to learn our white paper, Software program Invoice of Supplies Framework: Leveraging SBOMs for Threat Discount. If you happen to’re curious about piloting the framework or collaborating on future work, contact us at information@sei.cmu.edu.
