
Hackers are exploiting a essential vulnerability that impacts all D-Hyperlink DIR-859 WiFi routers to gather account info from the gadget, together with passwords.
The safety concern was disclosed in January and is at the moment tracked as CVE-2024-0769 (9.8 severity rating) – a path traversal flaw that results in info disclosure.
Though D-Hyperlink DIR-859 WiFi router mannequin reached end-of-life (EoL) and not receives any updates, the seller nonetheless launched a safety advisory explaining that the flaw exists within the “fatlady.php” file of the gadget, impacts all firmware variations, and permits attackers to leak session information, obtain privilege escalation, and achieve full management by way of the admin panel.
D-Hyperlink is just not anticipated to launch a fixing patch for CVE-2024-0769, so homeowners of the gadget ought to change to a supported gadget as quickly as doable.
Detected exploitation exercise
Risk monitoring platform GreyNoise has noticed the energetic exploitation of CVE-2024-0769 in assaults that depend on a slight variation of the general public exploit.
The researchers clarify that hackers are concentrating on the ‘DEVICE.ACCOUNT.xml’ file to dump all account names, passwords, consumer teams, and consumer descriptions current on the gadget.
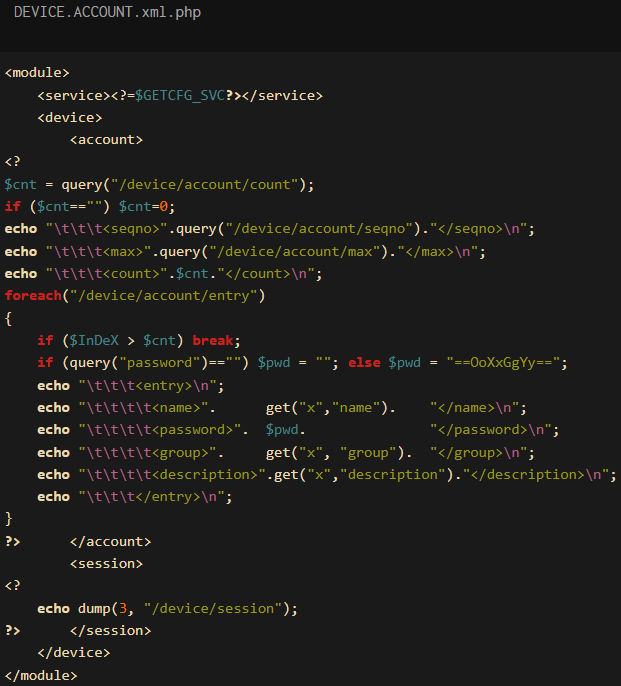
Supply: GreyNoise
The assault leverages a malicious POST request to ‘/hedwig.cgi,’ exploiting CVE-2024-0769 to entry delicate configuration recordsdata (‘getcfg’) by way of the ‘fatlady.php’ file, which doubtlessly incorporates consumer credentials.
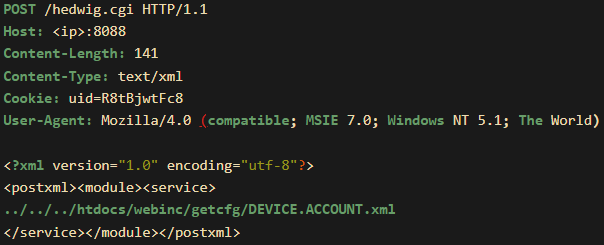
Supply: GreyNoise
GreyNoise has not decided the motivation of the attackers, however the concentrating on of consumer passwords reveals an intention to carry out gadget takeover, thus giving the attacker full management of the gadget.
“It’s unclear presently what the supposed use of this disclosed info is, it needs to be famous that these units won’t ever obtain a patch,” the researchers clarify.
“Any info disclosed from the gadget will stay beneficial to attackers for the lifetime of the gadget so long as it stays web dealing with” – GreyNoise
GreyNoise notes that the public proof-of-concept exploit, on which present assaults rely, targets the ‘DHCPS6.BRIDGE-1.xml’ file as an alternative of ‘DEVICE.ACCOUNT.xml’, so it could possibly be used to focus on different configuration recordsdata, together with:
- ACL.xml.php
- ROUTE.STATIC.xml.php
- INET.WAN-1.xml.php
- WIFI.WLAN-1.xml.php
These recordsdata might expose configurations for entry management lists (ACLs), NAT, firewall settings, gadget accounts, and diagnostics, so defenders ought to concentrate on them being potential targets for exploitation.
GreyNoise makes out there a bigger listing of recordsdata that could possibly be invoked in assaults that exploit CVE-2024-0769. This could server defenders in case different variations happen.
