Fortinet is warning of two new unpatched patch bypasses for a essential distant code execution vulnerability in FortiSIEM, Fortinet’s SIEM answer.
Fortinet added the 2 new vulnerabilities tracked as CVE-2024-23108 and CVE-2024-23109 to the unique advisory for the CVE-2023-34992 flaw in a really complicated replace.
Earlier immediately, BleepingComputer printed an article that the CVEs have been launched by mistake after being instructed by Fortinet that they have been duplicates of the unique CVE-2023-34992.
“On this occasion, as a consequence of a problem with the API which we’re presently investigating, somewhat than an edit, this resulted in two new CVEs being created, duplicates of the unique CVE-2023-34992,” Fortinet instructed BleepingComputer.
“There isn’t any new vulnerability printed for FortiSIEM to date in 2024, it is a system degree error and we’re working to rectify and withdraw the misguided entries.”
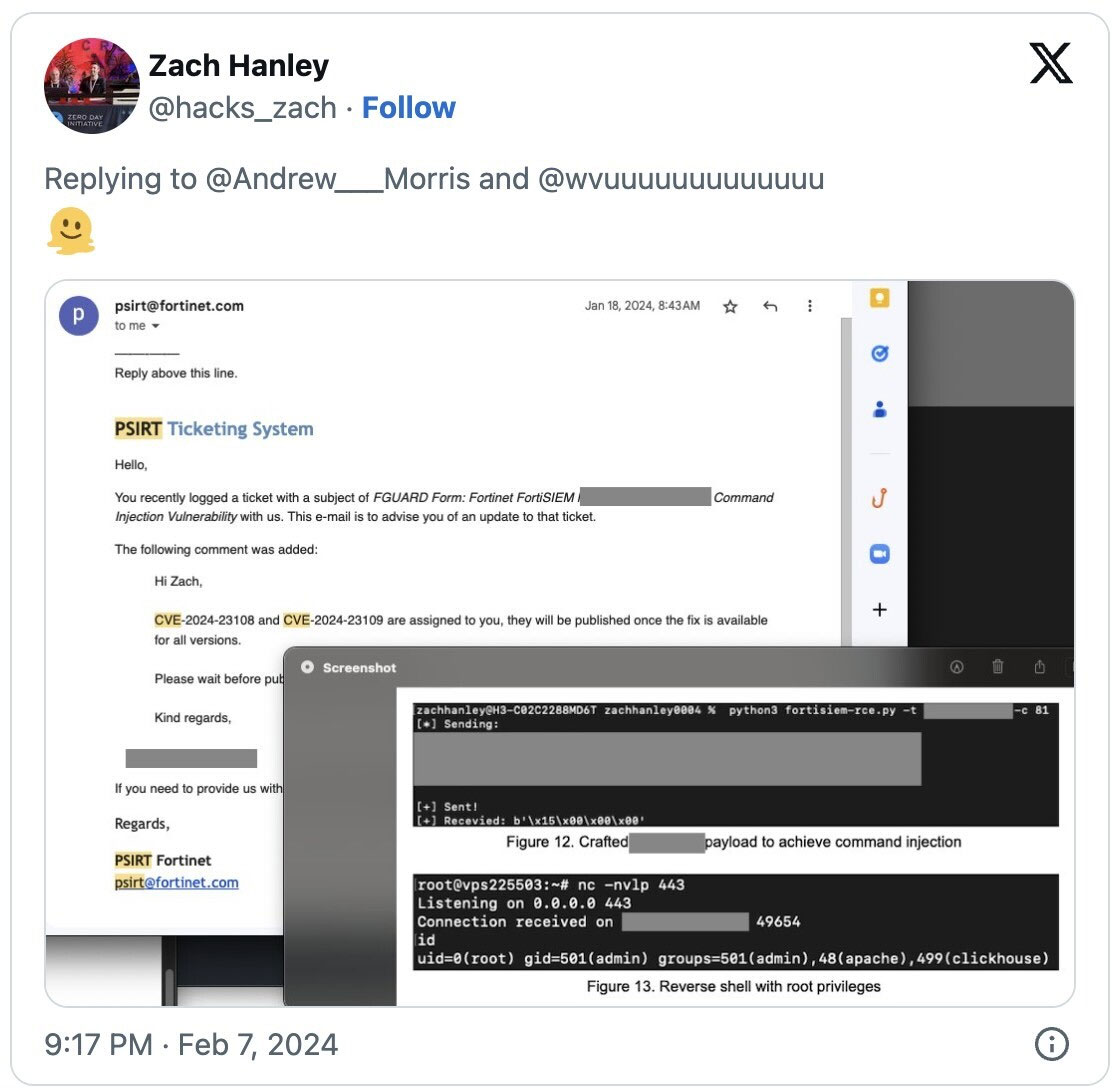
Nonetheless, it seems that CVE-2024-23108 and CVE-2024-23109 are literally patch bypasses for the CVE-2023-34992 flaw found by Horizon3 vulnerability skilled Zach Hanley.
On X, Zach said that the brand new CVEs are patch bypasses for CVE-2023-34992, and the brand new IDs have been assigned to him by Fortinet.
After contacting Fortinet as soon as once more, we have been instructed their earlier assertion was “misstated” and that the 2 new CVEs are variants of the unique flaw.
“The PSIRT staff adopted its course of so as to add two comparable variants of the earlier CVE (CVE-2023-34992), tracked as CVE-2024-23108 and CVE-2024-23109 to our public advisory FG-IR-23-130, which was printed in October 2023. The 2 new CVEs share the very same description and rating because the preliminary one; in parallel we up to date MITRE. A reminder pointing to the up to date Advisory shall be included for our prospects on Tuesday when Fortinet publishes its month-to-month advisory.” – Fortinet.
These two new variants have the identical description as the unique flaw, permitting unauthenticated attackers to execute instructions by way of specifically crafted API requests.
“A number of improper neutralization of particular components utilized in an OS Command vulnerability [CWE-78] in FortiSIEM supervisor might enable a distant unauthenticated attacker to execute unauthorized instructions by way of crafted API requests,” reads the advisory.
Whereas the unique flaw, CVE-2023-34992, was fastened in a earlier FortiSIEM launch, the brand new variants shall be fastened or have been fastened within the following variations:
- FortiSIEM model 7.1.2 or above
- Upcoming FortiSIEM model 7.2.0 or above
- Upcoming FortiSIEM model 7.0.3 or above
- Upcoming FortiSIEM model 6.7.9 or above
- Upcoming FortiSIEM model 6.6.5 or above
- Upcoming FortiSIEM model 6.5.3 or above
- Upcoming FortiSIEM model 6.4.4 or above
As it is a essential flaw, it’s strongly suggested that you just improve to one of many above FortiSIEM variations as quickly as they turn out to be out there.
Fortinet flaws are generally focused by risk actors, together with ransomware gangs, who use them to achieve preliminary entry to company networks, so patching rapidly is essential.
BleepingComputer requested Fortinet when the opposite variations shall be launched and can replace this story once we obtain a response.