
A brand new marketing campaign tracked as “Dev Popper” is focusing on software program builders with pretend job interviews in an try and trick them into putting in a Python distant entry trojan (RAT).
The builders are requested to carry out duties supposedly associated to the interview, like downloading and working code from GitHub, in an effort to make the whole course of seem official.
Nonetheless, the menace actor’s purpose is make their targets obtain malicious software program that gathers system data and permits distant entry to the host.
In keeping with Securonix analysts, the marketing campaign is probably going orchestrated by North Korean menace actors primarily based on the noticed ways. The connections should not robust sufficient for attribution, although.
Multi-stage an infection chain
“Dev Popper” assaults contain a multi-stage an infection chain primarily based on social engineering, designed to deceive targets via a means of progressive compromise.
The attackers provoke contact by posing as employers that supply trying to fill software program developer positions. Throughout the interview, the candidates are requested to obtain and run what’s offered as a normal coding job from a GitHub repository.
The file is a ZIP archive containing an NPM bundle, which has a README.md in addition to frontend and backend directories.
As soon as the developer runs the NPM bundle, an obfuscated JavaScript file (“imageDetails.js”) hidden contained in the backend listing is activated, executing ‘curl’ instructions via the Node.js course of to obtain an extra archive (“p.zi”) from an exterior server.

Securonix
Contained in the archive is the subsequent stage payload, an obfuscated Python script (“npl”) that features as a RAT.
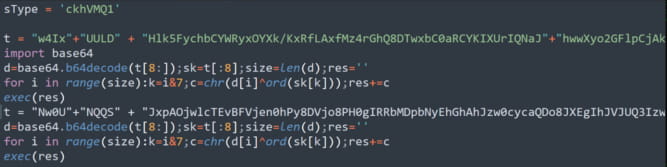
Securonix
As soon as the RAT is lively on the sufferer’s system, it collects and sends fundamental system data to the command and management (C2) server, together with OS kind, hostname, and community information.
Securonix stories that the RAT helps the next capabilities:
- Persistent connections for ongoing management.
- File system instructions to seek for and steal particular recordsdata or information.
- Distant command execution capabilities for extra exploits or malware deployment.
- Direct FTP information exfiltration from high-interest folders equivalent to ‘Paperwork’ and ‘Downloads.’
- Clipboard and keystroke logging to observe person exercise and probably seize credentials.
Though the perpetrators of the Dev Popper assault aren’t recognized, the tactic of utilizing job lures as bait to contaminate individuals with malware remains to be prevalent, so individuals ought to stay vigilant of the dangers.
The researchers observe that the strategy “exploits the developer’s skilled engagement and belief within the job utility course of, the place refusal to carry out the interviewer’s actions may compromise the job alternative,” which makes it very efficient.
North Korean hackers have been utilizing the “pretend job provide” tactic for a number of operations through the years to compromise their targets over varied platforms.
There have been quite a few stories [1, 2, 3, 4, 5] final yr about North Korean hacking teams utilizing pretend job alternatives to hook up with and compromise safety researchers, media organizations, software program builders (particularly for DeFi platforms), or workers of aerospace firms.
In a spear-phishing assault, the menace actor impersonated journalists to gather intelligence from suppose tanks, analysis hubs, and educational organizations.
