A number of proof-of-concept (PoC) exploits for a important Jenkins vulnerability permitting unauthenticated attackers to learn arbitrary information have been made publicly obtainable, with some researchers reporting attackers actively exploiting the issues in assaults.
Jenkins is an open-source automation server broadly utilized in software program improvement, significantly for Steady Integration (CI) and Steady Deployment (CD).
It performs a important position in automating numerous elements of the software program improvement course of, like constructing, testing, and deploying functions. It helps over a thousand integration plugins and is utilized by organizations of all sizes, together with massive enterprises.
SonarSource researchers found two flaws in Jenkins that might allow assaults to entry information in susceptible servers and execute arbitrary CLI instructions below sure circumstances.
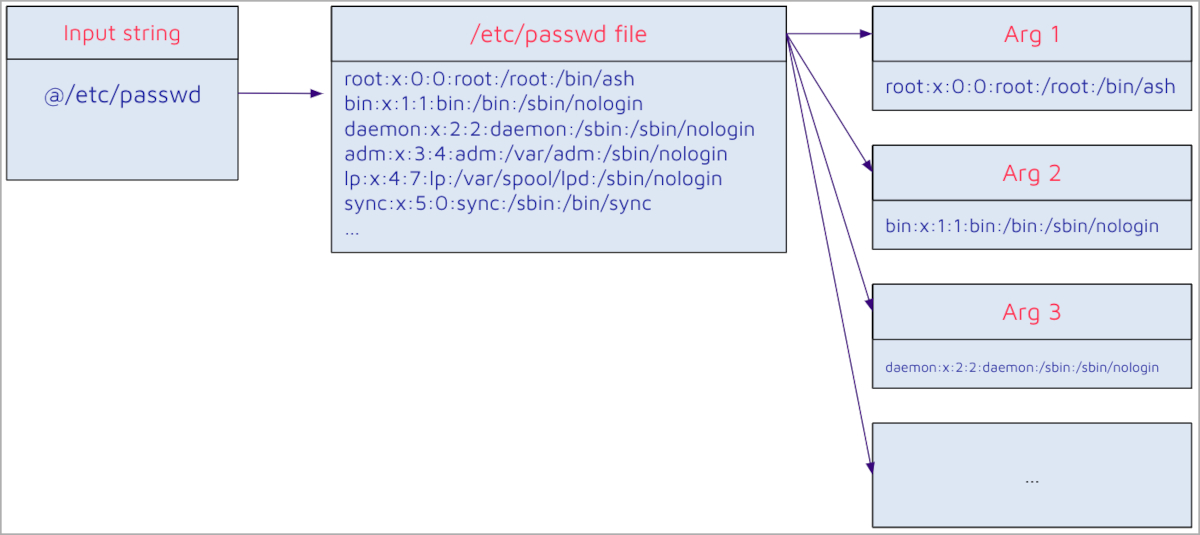
The primary flaw, rated important, is CVE-2024-23897, permitting unauthenticated attackers with ‘general/learn’ permission to learn information from arbitrary information on the Jenkins server.
Attackers with out this permission can nonetheless learn the primary few traces of information, with the quantity relying on the obtainable CLI instructions.
The flaw stems from the default habits of the args4j command parser in Jenkins, which routinely expands file contents into command arguments when an argument begins with the “@” character, permitting unauthorized studying of arbitrary information on the Jenkins controller file system.
Sonar defined that exploitation of the actual flaw might result in admin privilege escalation and arbitrary distant code execution. This step, nevertheless, is determined by sure circumstances that should be met, that are totally different for every assault variant.
The second flaw, tracked as CVE-2024-23898, is a cross-site WebSocket hijacking concern the place attackers might execute arbitrary CLI instructions by tricking a person into clicking a malicious hyperlink.
This danger that arises from this bug ought to be mitigated by current protecting insurance policies in internet browsers, nevertheless it persists as a result of lack of common enforcement of those insurance policies.
SonarSource reported the issues to the Jenkins safety crew on November 13, 2023, and helped confirm the fixes within the following months.
On January 24, 2024, Jenkins launched fixes for the 2 flaws with variations 2.442 and LTS 2.426.3, and printed an advisory that shares numerous assault situations and exploitation pathways, in addition to repair descriptions and doable workarounds for these unable to use the safety updates.
Exploits obtainable
With considerable details about the Jenkins flaws now obtainable, many researchers reproduced a number of the assault situations and created working PoC exploits printed on GitHub.
The PoCs are for CVE-2024-23897, which supplies attackers distant code execution on unpatched Jenkins servers.
Many of those PoCs have already been validated, so attackers scanning for uncovered servers can seize the scripts and take a look at them out with minimal or no modification.
Some researchers report that their Jenkins honeypots have already caught exercise within the wild, suggesting that hackers have began exploiting the vulnerabilities.