
Web big Cloudflare experiences that its DNS resolver service, 1.1.1.1, was lately unreachable or degraded for a few of its prospects due to a mixture of Border Gateway Protocol (BGP) hijacking and a route leak.
The incident occurred final week and affected 300 networks in 70 nations. Regardless of these numbers, the corporate says that the impression was “fairly low” and in some nations customers didn’t even discover it.
Incident particulars
Cloudflare says that at 18:51 UTC on June 27, Eletronet S.A. (AS267613) started saying the 1.1.1.1/32 IP deal with to its friends and upstream suppliers.
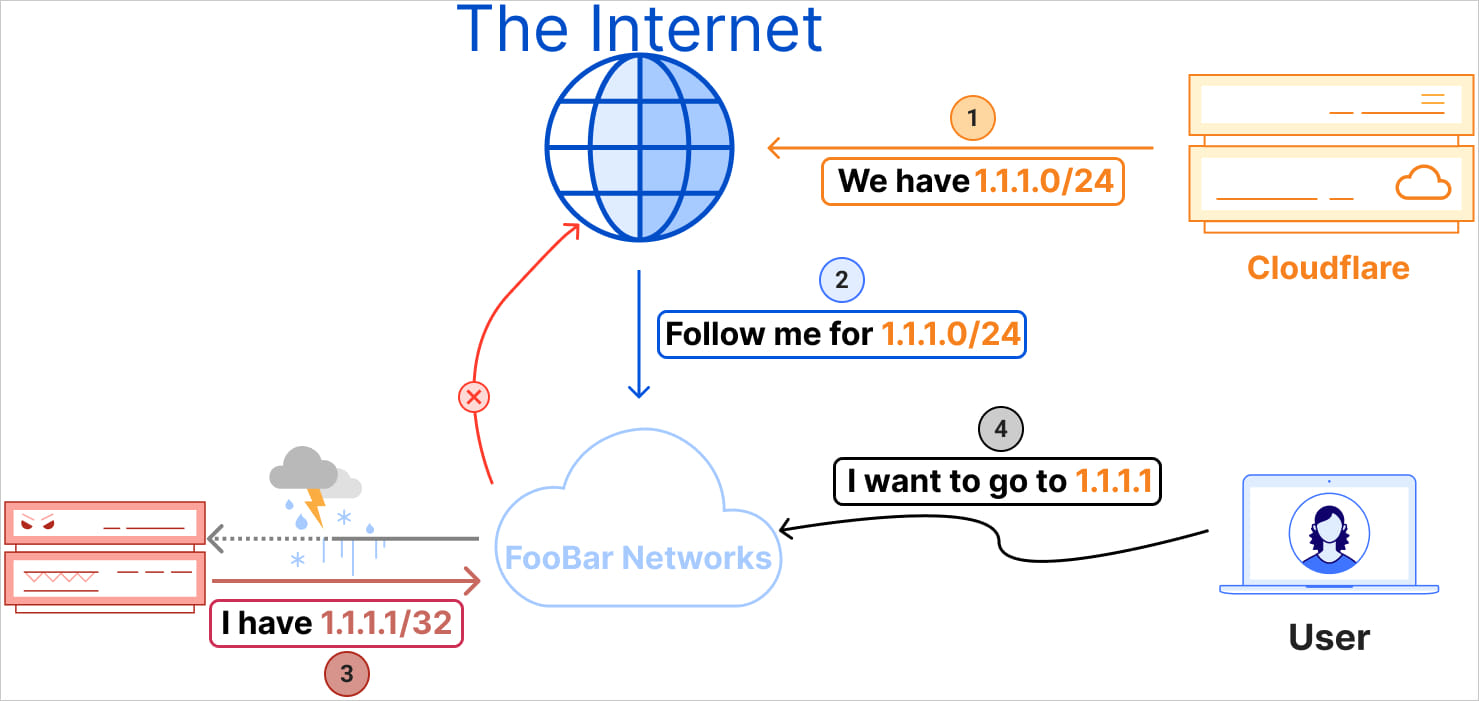
This incorrect announcement was accepted by a number of networks, together with a Tier 1 supplier, which handled it as a Distant Triggered Blackhole (RTBH) route.
The hijack occurred as a result of BGP routing favors essentially the most particular route. AS267613’s announcement of 1.1.1.1/32 was extra particular than Cloudflare’s 1.1.1.0/24, main networks to incorrectly route site visitors to AS267613.
Consequently, site visitors supposed for Cloudflare’s 1.1.1.1 DNS resolver was blackholed/rejected, and therefore, the service grew to become unavailable for some customers.
One minute later, at 18:52 UTC, Nova Rede de Telecomunicações Ltda (AS262504) erroneously leaked 1.1.1.0/24 upstream to AS1031, which propagated it additional, affecting world routing.
This leak altered the conventional BGP routing paths, inflicting site visitors destined for 1.1.1.1 to be misrouted, compounding the hijacking drawback and inflicting extra reachability and latency issues.
Cloudflare recognized the issues at round 20:00 UTC and resolved the hijack roughly two hours later. The route leak was resolved at 02:28 UTC.
Remediation effort
Cloudflare’s first line of response was to have interaction with the networks concerned within the incident whereas additionally disabling peering classes with all problematic networks to mitigate the impression and forestall additional propagation of incorrect routes.
The corporate explains that the wrong bulletins didn’t have an effect on inside community routing as a result of adopting the Useful resource Public Key Infrastructure (RPKI), which led to routinely rejecting the invalid routes.
Lengthy-term options Cloudflare introduced in its postmortem write-up embody:
- Improve route leak detection methods by incorporating extra information sources and integrating real-time information factors.
- Promote the adoption of Useful resource Public Key Infrastructure (RPKI) for Route Origin Validation (ROV).
- Promote the adoption of the Mutually Agreed Norms for Routing Safety (MANRS) rules, which embody rejecting invalid prefix lengths and implementing strong filtering mechanisms.
- Encourage networks to reject IPv4 prefixes longer than /24 within the Default-Free Zone (DFZ).
- Advocate for deploying ASPA objects (at the moment drafted by the IETF), that are used to validate the AS path in BGP bulletins.
- Discover the potential of implementing RFC9234 and Discard Origin Authorization (DOA).
