
Cyberespionage teams have been utilizing ransomware as a tactic to make assault attribution tougher, distract defenders, or for a monetary reward as a secondary purpose to information theft.
A joint report from SentinelLabs and Recorded Future analysts presents the case of ChamelGang, a suspected Chinese language superior persistent risk (APT) that has been utilizing the CatB ransomware pressure in assaults that impression high-profile organizations worldwide.
A separate exercise cluster makes use of BestCrypt and Microsoft BitLocker to realize comparable objectives, though attribution just isn’t clear.
ChamelGang focusing on
ChamelGang is also called CamoFei and has focused authorities organizations and important infrastructure entities between 2021 and 2023.
The group makes use of refined methods to achieve preliminary entry, for reconnaissance and lateral motion, and to exfiltrate delicate information.
In an assault in November 2022, the risk actors focused the Presidency of Brazil and compromised 192 computer systems. The adversary relied on customary reconnaissance instruments to map the community and to assemble info on important programs.
Within the final stage of the assault, ChamelGang deployed CatB ransomware on the community, dropping ransom notes originally of every encrypted file. They supplied a ProtonMail handle for contact and a Bitcoin handle for fee.
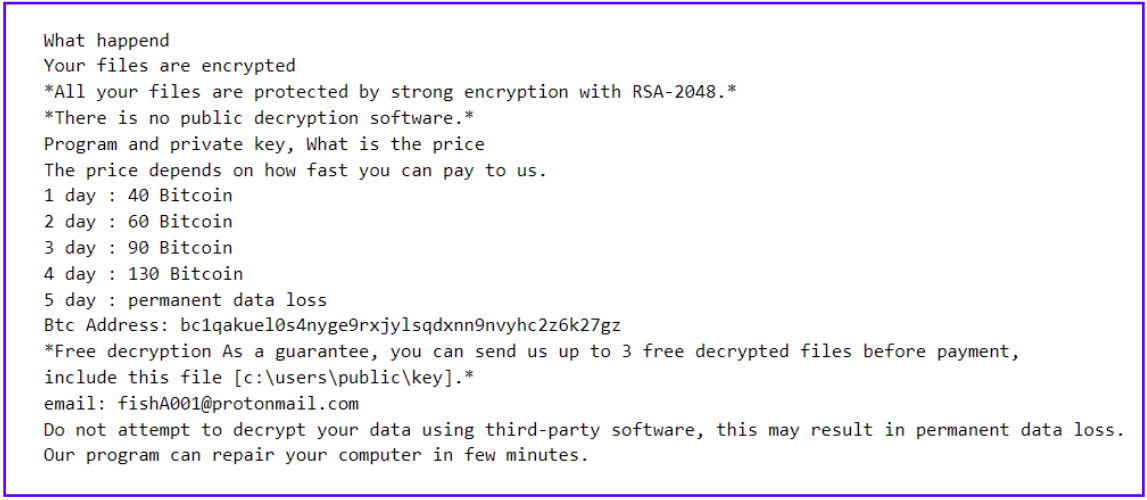
Supply: SentinelLabs
The assault was initially attributed to TeslaCrypt however SentinelLabs and Recorded Future current new proof that time to ChamelGang.
Throughout one other incident in late 2022, ChamelGang breached the All India Institute Of Medical Sciences (AIIMS) public medical analysis college and hospital. The risk actor used CatB ransomware as soon as once more, inflicting main disruptions in healthcare providers.
The researchers imagine that two different assaults, towards a authorities entity in East Asia and an aviation group within the Indian subcontinent are additionally the work of ChamelGang, based mostly on the usage of identified TTPs, publicly out there tooling seen in earlier engagements, and their customized malware BeaconLoader.
BestCrypt and BitLocker
A separate cluster of actions noticed by SentinelLabs and Recorded Future encrypts recordsdata utilizing Jetico BestCrypt and Microsoft BitLocker as an alternative of CatB ransomware.
The researchers say that these intrusions impacted 37 organizations, most of them in North America. Different victims have been in South America and Europe.
By evaluating proof in reviews from different cybersecurity firms, the researchers found overlaps with previous intrusions linked to suspected Chinese language and North Korean APTs.
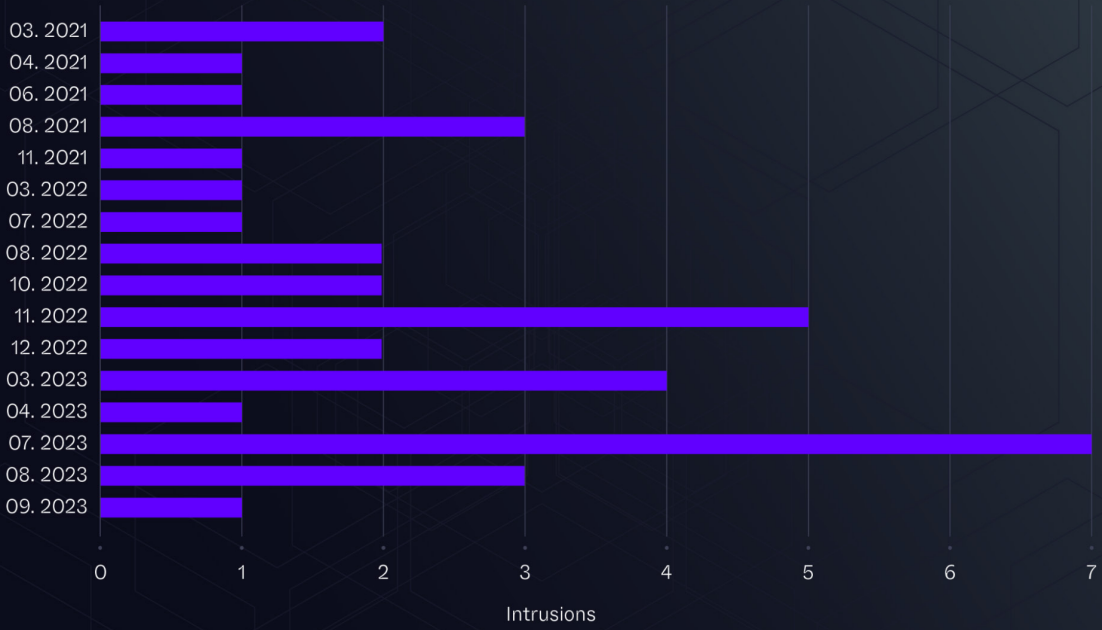
Supply: SentinelLabs
Usually, BestCrypt was used to focus on server endpoints in an automatic, serial encryption method, whereas BitLocker was deployed towards workstations, with distinctive restoration passwords utilized in every case.
The attackers additionally used the China Chopper webshell, a customized variant of the miPing software, and leveraged Energetic Listing Area Controllers (DCs) as footholds.
The analysts report these assaults lasted for 9 days on common, whereas some had a brief period of simply a few hours, indicating familiarity with the focused surroundings.
A motive for involving ransomware in cyberespionage assaults might be that it offers strategic and operational advantages that blur the strains between APT and cybercriminal exercise, which might result in incorrect attribution or as a way to hide the info assortment nature of the operation.
Attributing previous ransomware incidents to a cyberespionage risk actor as ChamelGang is new and exhibits that adversaries are altering ways to cowl their tracks whereas nonetheless attaining their objectives.
