Cyber safety researchers have uncovered a vulnerability within the RADIUS protocol, dubbed BlastRADIUS. Whereas there isn’t a proof that menace actors are actively exploiting it, the group is looking for each RADIUS server to be upgraded.
A BlastRADIUS assault includes the attacker intercepting community site visitors between a consumer, akin to a router, and the RADIUS server. The attacker can then manipulate the MD5 hashing algorithm such that an Entry-Denied community packet is learn as Entry-Settle for. This gives them entry to the consumer gadget with out the proper login credentials.
A group of researchers from Boston College, Cloudflare, BastionZero, Microsoft Analysis, Centrum Wiskunde & Informatica and the College of California, San Diego first found the vulnerability in February and notified Alan DeKok, chief govt officer of InkBridge Networks and RADIUS professional.
The BlastRADIUS flaw, now tracked as CVE-2024-3596 and VU#456537, is because of a “basic design flaw of the RADIUS protocol,” in response to a safety announcement from the RADIUS server FreeRADIUS, maintained by DeKok. Subsequently, it isn’t restricted to a single product or vendor.
SEE: Methods to use FreeRADIUS for SSH authentication
“Community technicians should set up a firmware improve and reconfigure primarily each change, router, GGSN, BNG, and VPN concentrator around the globe,” DeKok mentioned in a press launch. “We anticipate to see a whole lot of speak and exercise associated to RADIUS safety within the subsequent few weeks.”
What’s the RADIUS protocol?
RADIUS, or Distant Authentication Dial-In Consumer Service, is a networking protocol that gives centralised authentication, authorisation and accounting for customers connecting to a community service. It’s extensively utilized by web service suppliers and enterprises for switches, routers, entry servers, firewalls and VPN merchandise.
Who’s affected by the BlastRADIUS flaw?
Researchers discovered that RADIUS deployments that use PAP, CHAP, MS-CHAP and RADIUS/UDP over the web shall be affected by the BlastRADIUS flaw. Which means that ISPs, cloud identification suppliers, telecommunication corporations and enterprises with inside networks are in danger and should take swift motion, particularly if RADIUS is used for administrator logins.
People utilizing the web from residence will not be straight susceptible, however they do depend on their ISP resolving the BlastRADIUS flaw, or else their site visitors might be directed to a system below the attacker’s management.
Enterprises utilizing PSEC, TLS or 802.1X protocols, in addition to providers like eduroam or OpenRoaming, are all thought of secure.
How does a BlastRADIUS assault work?
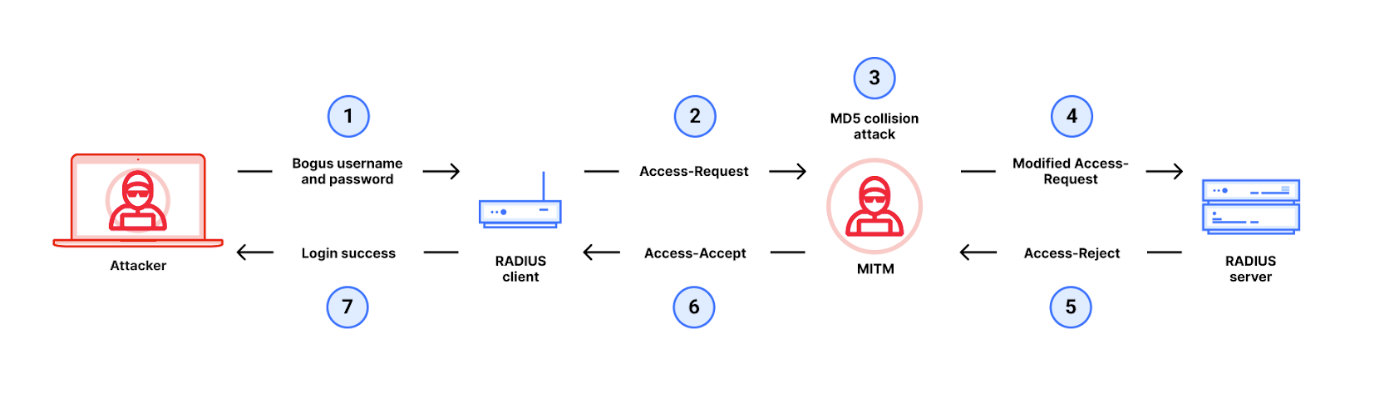
Exploiting the vulnerability leverages a man-in-the-middle assault on the RADIUS authentication course of. It hinges on the truth that, within the RADIUS protocol, some Entry-Request packets will not be authenticated and lack integrity checks.
An attacker will begin by making an attempt to log in to the consumer with incorrect credentials, producing an Entry-Request message that’s despatched to the server. The message is shipped with a 16-byte worth known as a Request Authenticator, generated via MD5 hashing.
The Request Authenticator is meant for use by the recipient server to compute its response together with a so-called “shared secret” that solely the consumer and server know. So, when the consumer receives the response, it might decipher the packet utilizing its Request Authenticator and the shared secret, and confirm that it was despatched by the trusted server.
However, in a BlastRADIUS assault, the attacker intercepts and manipulates the Entry-Request message earlier than it reaches the server in an MD5 collision assault. The attacker provides “rubbish” knowledge to the Entry-Request message, making certain the server’s Entry-Denied response additionally consists of this knowledge. Then, they manipulate this Entry-Denied response such that it’s learn by the consumer as a sound Entry-Settle for message, granting them unauthorised entry.
Whereas MD5 is well-known to have weaknesses that enable attackers to generate collisions or reverse the hash, the researchers say that the BlastRADIUS assault “is extra complicated than merely making use of an outdated MD5 collision assault” and extra superior when it comes to velocity and scale. That is the primary time an MD5 assault has been virtually demonstrated towards the RADIUS protocol.
Researchers at Cloudflare carried out the assault on RADIUS gadgets with a timeout interval of 5 minutes. Nevertheless, there’s scope for attackers with refined computing sources to carry out it in considerably much less time, probably between 30 and 60 seconds, which is the default timeout interval for a lot of RADIUS gadgets.
“The important thing to the assault is that in lots of circumstances, Entry-Request packets haven’t any authentication or integrity checks,” documentation from InkBridge Networks reads. “An attacker can then carry out a selected prefix assault, which permits modifying the Entry-Request so as to exchange a sound response with one chosen by the attacker.
“Despite the fact that the response is authenticated and integrity checked, the chosen prefix vulnerability permits the attacker to change the response packet, virtually at will.”
You’ll be able to learn a full technical description and proof-of-concept of a BlastRADIUS assault on this PDF.
How straightforward is it for an attacker to take advantage of the BlastRADIUS vulnerability?
Whereas the BlastRADIUS flaw is pervasive, exploiting it isn’t trivial; the attacker wants to have the ability to learn, intercept, block and modify inbound and outbound community packets, and there’s no publicly-available exploit for them to check with. The attacker additionally will need to have current community entry, which might be acquired by benefiting from an organisation sending RADIUS/UDP over the open web or by compromising a part of the enterprise community.
“Even when RADIUS site visitors is confined to a protected a part of an inside community, configuration or routing errors would possibly unintentionally expose this site visitors,” the researchers mentioned on a web site devoted to BlastRADIUS. “An attacker with partial community entry could possibly exploit DHCP or different mechanisms to trigger sufferer gadgets to ship site visitors outdoors of a devoted VPN.”
Moreover, the attacker have to be well-funded, as a big quantity of cloud computing energy is required to drag off every BlastRADIUS assault. InkBridge Networks states in its BlastRADIUS FAQs that such prices could be a “drop within the bucket for nation-states who want to goal explicit customers.”
How organisations can defend themselves from a BlastRADIUS assault
The safety researchers have offered the next suggestions for organisations that use the RADIUS protocol:
- Set up the newest updates on all RADIUS purchasers and servers made out there by the seller. Patches have been deployed to make sure Message-Authenticator attributes are at all times despatched and required for requests and responses. There may be an up to date model of FreeRADIUS out there for obtain, and Palo Alto Networks has additionally revealed fixes for its PAN-OS firewalls.
- Don’t attempt to replace all of the RADIUS gear directly, as errors might be made. Ideally, think about upgrading the RADIUS servers first.
- Think about using InkBridge Networks’ verification instruments that assess a system’s publicity to BlastRADIUS and different community infrastructure points.
Extra detailed directions for system directors will be discovered on the FreeRADIUS web site.
