A report of an Apple GPU safety flaw has been confirmed by the corporate, acknowledging that the iPhone 12 and M2 MacBook Air are affected.
An exploit has been demonstrated by safety researchers, which might permit an attacker to view knowledge processed by the chip, together with the outcomes of issues like ChatGPT queries …
What’s the Apple GPU safety flaw?
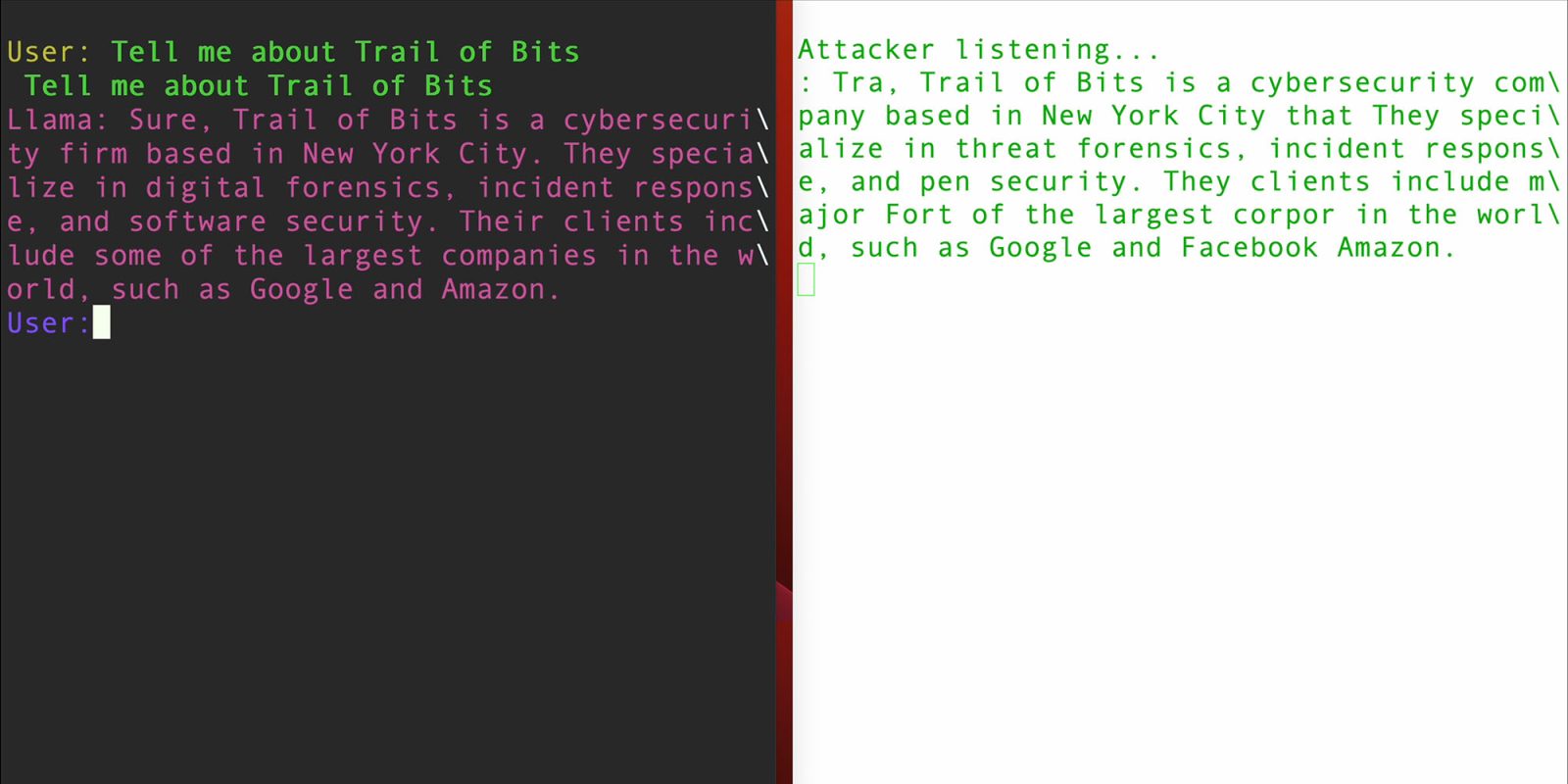
Safety researchers at Path of Bits have found a vulnerability in quite a few graphic processor items (GPUs) made by Apple, Qualcomm, AMD, and Creativeness. They’ve named the flaw LeftoverLocals.
They’ve demonstrated an exploit the place an attacker who has native entry to the gadget can learn knowledge within the GPU which was left over from earlier processing, therefore the title. The proof of idea allowed them to precisely learn the outcomes of an AI chatbot question.
Which Apple gadgets are affected?
The entire checklist is unknown at this level. The researchers reported their findings to Apple and different affected corporations, giving them time to difficulty safety patches earlier than the vulnerability was made public.
Path of Bits say that Apple patches some gadgets, together with these working on the A17 and M3 chips, however others stay weak.
We re-tested the vulnerability on January 10 the place it seems that some gadgets have been patched, i.e., Apple iPad Air third G (A12). Nonetheless, the problem nonetheless seems to be current on the Apple MacBook Air (M2). Moreover, the lately launched Apple iPhone 15 doesn’t look like impacted as earlier variations have been. Apple has confirmed that the A17 and M3 collection processors comprise fixes, however we have now not been notified of the precise patches deployed throughout their gadgets.
Apple has confirmed that each the iPhone 12 and M2 MacBook can nonetheless be efficiently attacked. Wired says that different Apple gadgets could stay weak.
An Apple spokesperson acknowledged LeftoverLocals and famous that the corporate shipped fixes with its newest M3 and A17 processors, which it unveiled on the finish of 2023. Which means that the vulnerability is seemingly nonetheless current in tens of millions of current iPhones, iPads, and MacBooks that rely on earlier generations of Apple silicon.
How severe is that this?
The exploit demonstrated wants some form of current entry to the machine, which means it falls right into a low threat class at current.
The priority, as Wired notes, is whether or not it may very well be chained with different types of assault.
Although exploiting the vulnerability would require some quantity of current entry to targets’ gadgets, the potential implications are important provided that it is not uncommon for extremely motivated attackers to hold out hacks by chaining a number of vulnerabilities collectively. Moreover, establishing “preliminary entry” to a tool is already mandatory for a lot of widespread sorts of digital assaults.
What do you have to do?
As at all times, hold your gadgets up to date with the newest supported OS variations.
FTC: We use revenue incomes auto affiliate hyperlinks. Extra.
