
A phishing marketing campaign detected in late November 2023 has compromised lots of of person accounts in dozens of Microsoft Azure environments, together with these of senior executives.
Hackers goal executives’ accounts as a result of they’ll entry confidential company info, self-approve fraudulent monetary transactions, and entry important programs to make use of them as a foothold for launching extra in depth assaults in opposition to the breached group or its companions.
Proofpoint’s Cloud Safety Response Workforce, which has been monitoring the malicious exercise, issued an alert earlier at present highlighting the lures the risk actors use and proposing focused protection measures.
Marketing campaign particulars
The assaults make use of paperwork despatched to targets that embed hyperlinks masqueraded as “View doc” buttons that take victims to phishing pages.
Proofpoint says the messages goal staff who usually tend to maintain increased privileges inside their using group, which elevates the worth of a profitable account compromise.
“The affected person base encompasses a large spectrum of positions, with frequent targets together with Gross sales Administrators, Account Managers, and Finance Managers. People holding government positions similar to “Vice President, Operations”, “Chief Monetary Officer & Treasurer” and “President & CEO” had been additionally amongst these focused,” explains Proofpoint.
The analysts recognized the next Linux user-agent string which attackers use to realize unauthorized entry to Microsoft365 apps:
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
This person agent has been related to numerous post-compromise actions, similar to MFA manipulation, information exfiltration, inner and exterior phishing, monetary fraud, and creating obfuscation guidelines in mailboxes.
Proofpoint says it has noticed unauthorized entry to the next Microsoft365 parts:
- Office365 Shell WCSS-Shopper: Signifies browser entry to Office365 functions, suggesting web-based interplay with the suite.
- Workplace 365 Change On-line: Exhibits that attackers goal this service for email-related abuses, together with information exfiltration and lateral phishing.
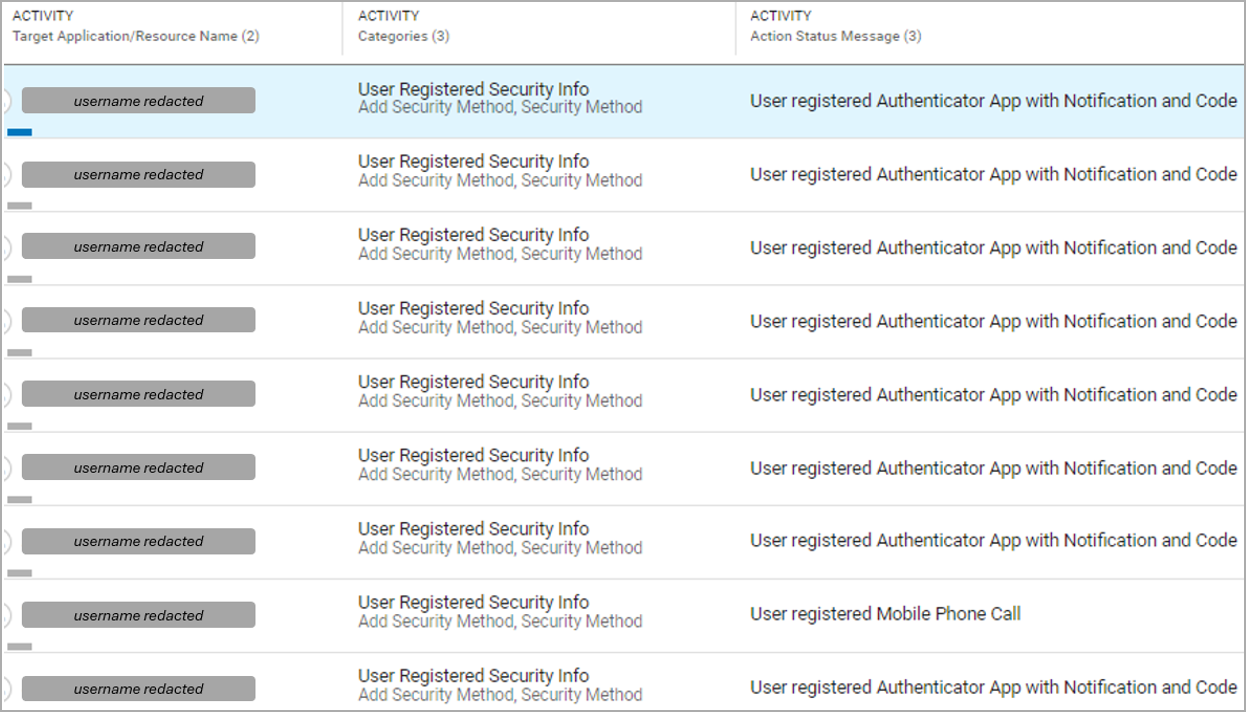
- My Signins: Utilized by attackers to govern Multi-Issue Authentication (MFA).
- My Apps: Focused for accessing and presumably altering configurations or permissions of functions throughout the Microsoft 365 setting.
- My Profile: Signifies makes an attempt to switch person private and safety settings, probably to keep up unauthorized entry or escalate privileges.
Proofpoint additionally studies that the attackers’ operational infrastructure contains proxies, information internet hosting companies, and hijacked domains. Proxies are chosen to be close to the targets to scale back the chance of assaults being blocked by MFA or different geo-fencing insurance policies.
The cybersecurity agency additionally noticed non-conclusive proof that the attackers could also be primarily based in Russia or Nigeria, primarily based on the usage of sure native fixed-line web service suppliers.
Easy methods to defend
Proofpoint proposes a number of protection measures to guard in opposition to the continued marketing campaign, which can assist improve organizational safety inside Microsoft Azure and Workplace 365 environments.
The recommendations embody:
- Monitor for the usage of the particular user-agent string shared above and supply domains in logs.
- Instantly reset compromised passwords of hijacked accounts and periodically change passwords for all customers.
- Use safety instruments to detect account takeover occasions rapidly.
- Apply industry-standard mitigations in opposition to phishing, brute-forcing, and password-spraying assaults.
- Implement insurance policies for computerized risk response.
These measures can assist detect incidents early, reply quickly, and decrease the attackers’ alternative and dwell instances as a lot as potential.
