
Main U.S. business financial institution Truist confirmed its techniques had been breached in an October 2023 cyberattack after a risk actor posted a number of the firm’s knowledge on the market on a hacking discussion board.
Headquartered in Charlotte, North Carolina, Truist Financial institution was fashioned after SunTrust Banks and BB&T (Department Banking and Belief Firm) merged in December 2019.
Now a top-10 business financial institution with whole belongings of $535 billion, Truist gives a variety of providers, together with client and small enterprise banking, business banking, company and funding banking, insurance coverage, wealth administration, and funds.
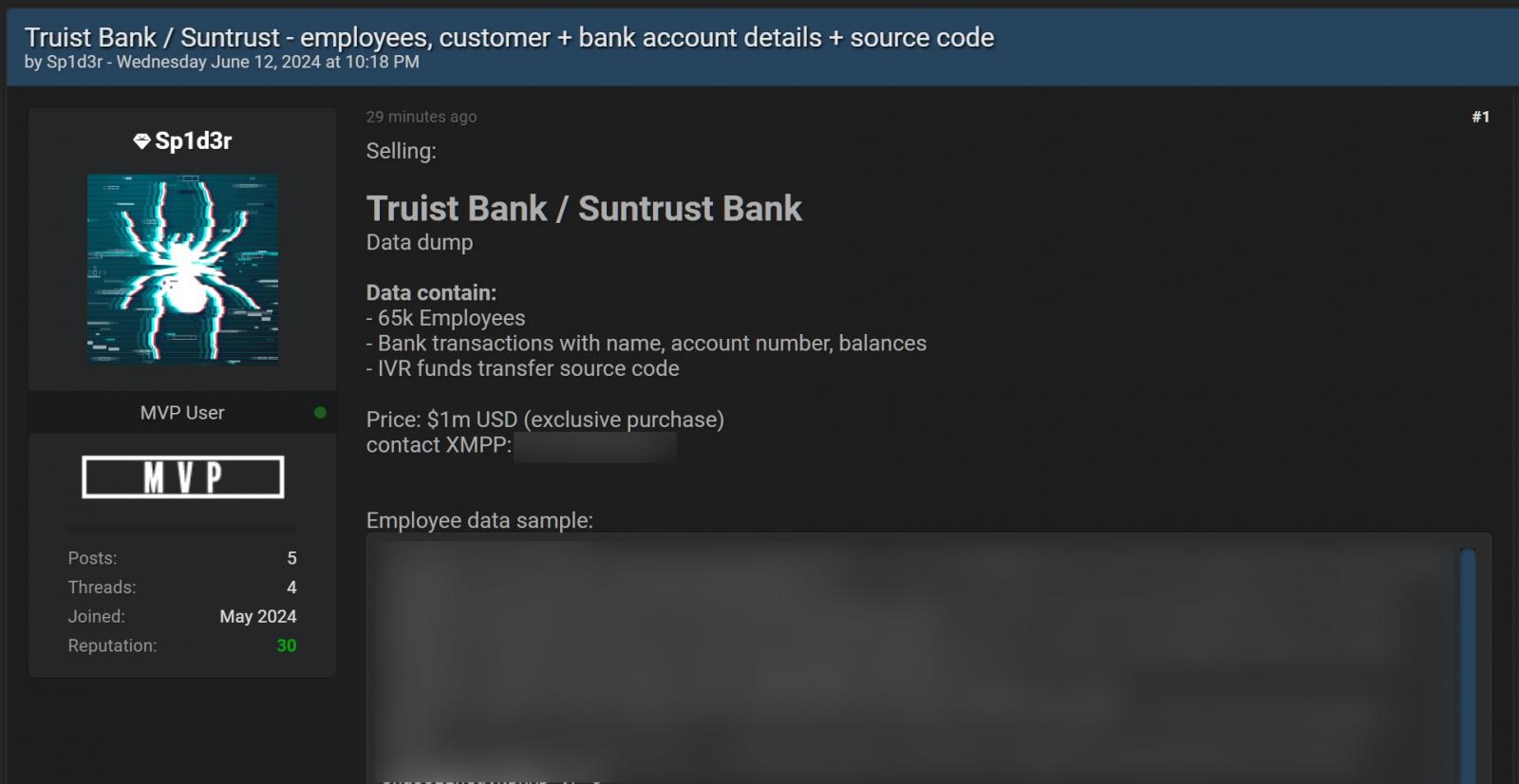
A risk actor (generally known as Sp1d3r) is promoting what they declare is stolen knowledge containing info belonging to 65,000 workers for $1 million, as first noticed by DarkTower intelligence analyst James Hub.
Whereas BleepingComputer couldn’t independently confirm these claims, the info additionally allegedly incorporates financial institution transactions with names, account numbers, balances, and IVR funds switch supply code.
”In October 2023, we skilled a cybersecurity incident that was shortly contained,” a Truist Financial institution spokesperson instructed BleepingComputer when requested to touch upon the risk actor’s claims.
“In partnership with exterior safety consultants, we carried out an intensive investigation, took extra measures to safe our techniques, and notified a small variety of purchasers final Fall,
When requested if this was related to the continuing Snowflake assaults, the spokesperson stated, “That incident will not be linked to Snowflake. To be clear, we have now discovered no proof of a Snowflake incident at our firm.”
“We recurrently work with regulation enforcement and outdoors cybersecurity consultants to assist shield our techniques and knowledge,” the Truist Financial institution spokesperson added.
“Primarily based on new info from the continuing investigation of the October 2023 incident, we have now notified extra purchasers. Now we have discovered no indication of fraud arising from this incident presently.”
The identical risk actor additionally sells knowledge stolen from cybersecurity firm Cylance for $750,000, together with databases allegedly containing 34,000,000 buyer and worker emails and personally identifiable info belonging to Cylance prospects, companions, and workers.
Cylance confirmed the legitimacy of their claims, stating that it is outdated knowledge (from 2015-2018) stolen from a “third-party platform.”
Sp1d3r additionally beforehand put up on the market 3TB of information belonging to automotive aftermarket components supplier Advance Auto Components on the identical hacking discussion board, stolen after breaching Advance’s Snowflake account.
