
An enormous trove of 361 million electronic mail addresses from credentials stolen by password-stealing malware, in credential stuffing assaults, and from knowledge breaches was added to the Have I Been Pwned knowledge breach notification service, permitting anybody to examine if their accounts have been compromised.
Cybersecurity researchers collected these credentials from quite a few Telegram cybercrime channels, the place the stolen knowledge is usually leaked to the channel’s customers to construct repute and subscribers.
The stolen knowledge is often leaked as username and password combos (often stolen through credential stuffing assaults or knowledge breaches), username and passwords together with a URL related to them (stolen through password-stealing malware), and uncooked cookies (stolen through password-stealing malware).
Supply: Troy Hunt (left) and BleepingComputer (proper)
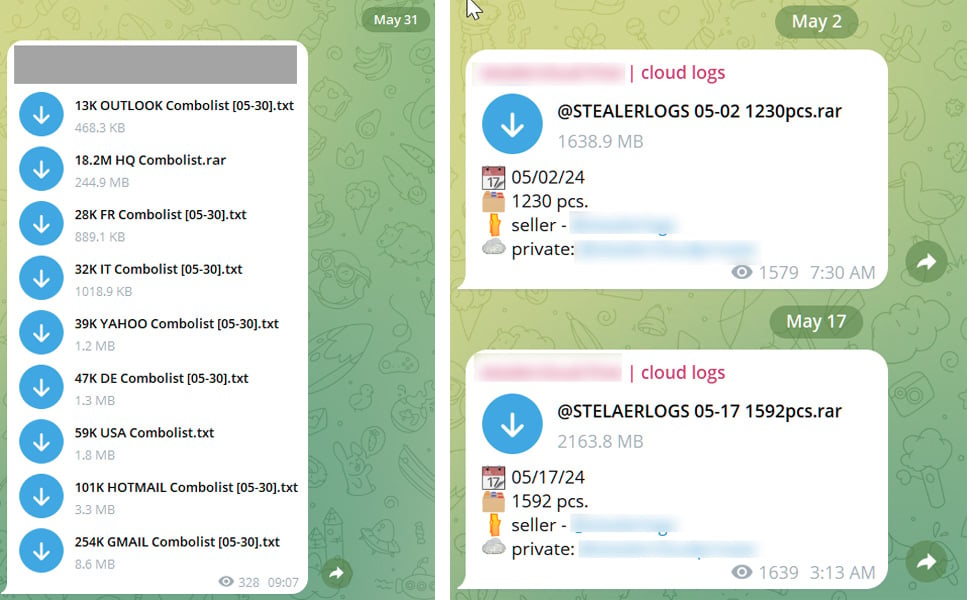
The researchers, who requested BleepingComputer to stay nameless, shared 122 GB of credentials with Troy Hunt, the proprietor of Have I Been Pwned, collected from many Telegram channels.
In keeping with Hunt, this knowledge is huge, containing 361 million distinctive electronic mail addresses, with 151 million by no means beforehand seen by the info breach notification service.
“It contained 1.7k information with 2B strains and 361M distinctive electronic mail addresses of which 151M had by no means been seen in HIBP earlier than,” posted Hunt.
“Alongside these addresses have been passwords and, in lots of instances, the web site the info pertains to.”
With a dataset this huge, it’s not possible to confirm that the entire leaked credentials are respectable.
Nonetheless, Hunt stated that he utilized websites’ password reset kinds to verify that many leaked electronic mail addresses are accurately related to the web site listed within the stolen credentials. Hunt couldn’t affirm the password, as that might require him to log into the account, which might be unlawful.
Supply: Troy Hunt
No web site unaffected
With a dataset this huge, no web site that enables logins is unaffected by these leaked credentials, together with BleepingComputer.
Final week, the identical researchers shared with BleepingComputer an inventory of credentials stolen by information-stealing malware related to the BleepingComputer boards.
Info-stealing malware is an an infection that steals passwords, cookies, browser historical past, cryptocurrency wallets, and different knowledge from an contaminated gadget.
This knowledge is compiled into an archive known as a “log” after which transmitted again to the menace actor’s servers, the place it’s bought on cybercrime marketplaces, shared with different menace actors, or used to breach a sufferer’s different accounts.
Such a malware is usually distributed by social media, cracked software program, faux VPN merchandise, or just by malicious electronic mail campaigns despatched by hacked gaming firm assist websites.
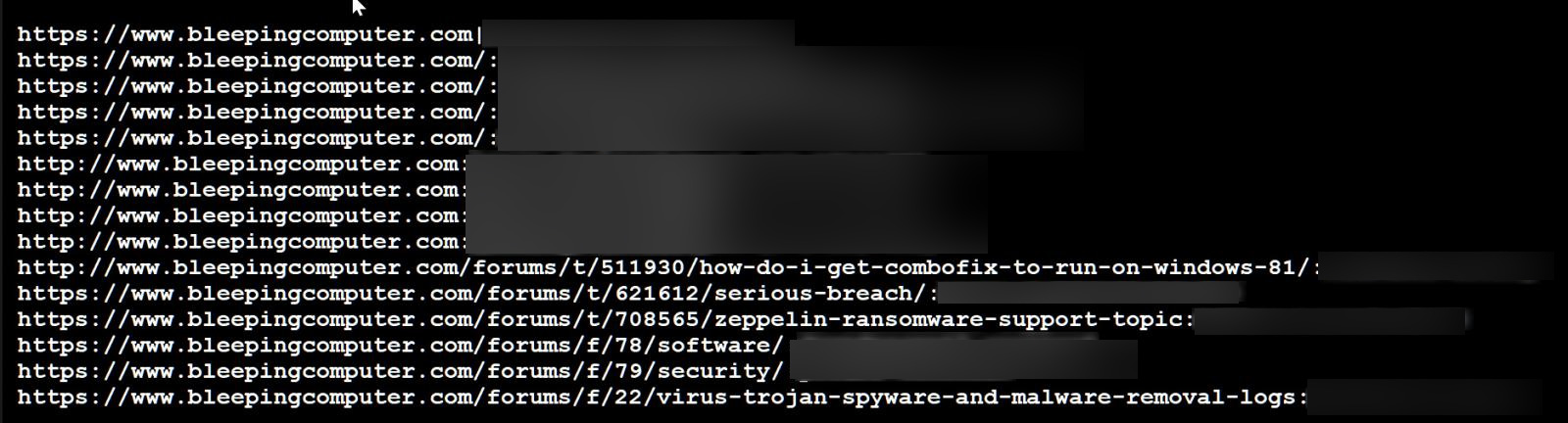
The info shared with BleepingCompute contains the username, password, and URL {that a} member used to log into our boards, which was then saved of their browser’s password supervisor.
Supply: BleepingComputer
As you’ll be able to see from the URLs above, many customers visited BleepingComputer as a result of they suspected their laptop was contaminated, which we now know was true.
BleepingComputer is at the moment analyzing the info and eradicating duplicates so we are able to proactively reset impacted members’ passwords and warn them that they have been contaminated sooner or later with information-stealing malware.
Customers who’re contaminated with information-stealing malware will now need to reset each password on each account that was saved of their browser’s password supervisor, and some other web site utilizing the identical credentials.
Sadly, stolen credentials are often not shared with a timestamp to point when they’re stolen. Subsequently, impacted customers should contemplate that each one of their credentials have been compromised.
Whereas this will likely be an arduous job, at the least they’ll know why their accounts and providers have exhibited unusual habits through the years.
BleepingComputer is usually contacted by individuals who inform us that their accounts constantly get hacked, even after they change the password again and again. These folks always report unusual habits on their gadgets or networks, however no malware infections are ever discovered.
The person can now achieve some closure, figuring out that they weren’t loopy, however that the malicious exercise is probably going attributed to their credentials beforehand being stolen and menace actors abusing them for their very own amusement or malicious exercise.
Info-stealing malware has turn into a scourge of cybersecurity, utilized by menace actors to conduct huge assaults, corresponding to ransomware and knowledge theft assaults.
Some well-known assaults attributable to credentials being stolen by info stealing malware, together with assaults on the Costa Rican authorities, Microsoft, CircleCi, and an account at Orange Spain RIPE that led to a intentional BGP misconfiguration.
Extra not too long ago menace actors stole knowledge from Snowflake databases utilizing what’s believed to be compromised credentials stolen utilizing information-stealing malware.
Sadly, there isn’t any straightforward answer to forestall information-stealing assaults, as they’re low complexity, making them have have huge distribution by quite a lot of assaults.
The perfect protection is to apply good cybersecurity habits, together with not opening attachments from untrusted sources, downloading software program solely from trusted sources, enabling file extensions in Home windows, utilizing antivirus software program, and preserving your software program up to date.
A extra detailed information associated to ransomware however nonetheless relevant will be discovered right here.
