
Since April, thousands and thousands of phishing emails have been despatched by means of the Phorpiex botnet to conduct a large-scale LockBit Black ransomware marketing campaign.
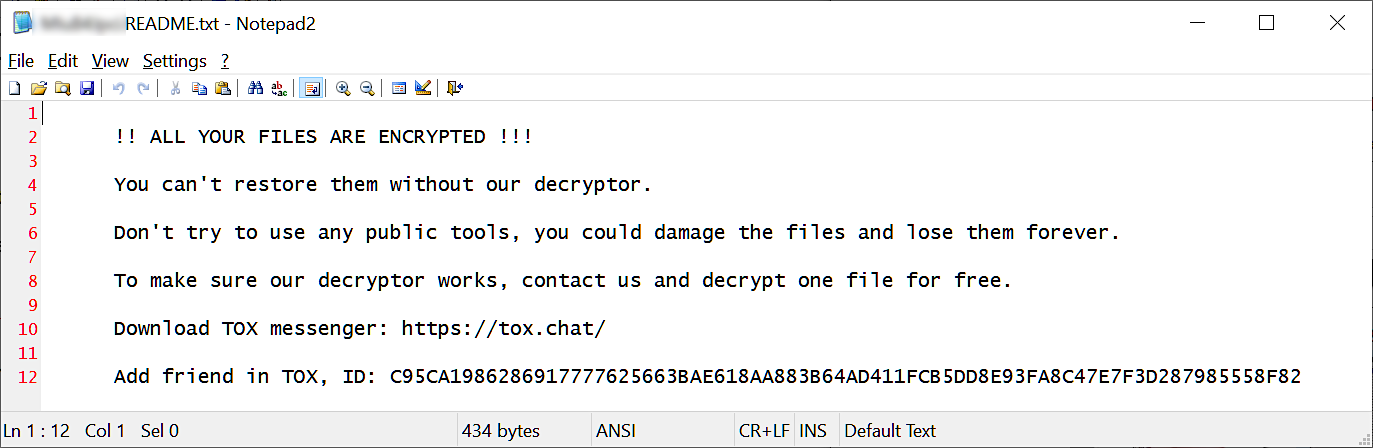
As New Jersey’s Cybersecurity and Communications Integration Cell (NJCCIC) warned on Friday, the attackers use ZIP attachments containing an executable that deploys the LockBit Black payload, which encrypts the recipients’ methods if launched.
The LockBit Black encryptor deployed in these assaults is probably going constructed utilizing the LockBit 3.0 builder leaked by a disgruntled developer on Twitter in September 2022. Nonetheless, this marketing campaign will not be believed to have any affiliation with the precise LockBit ransomware operation.
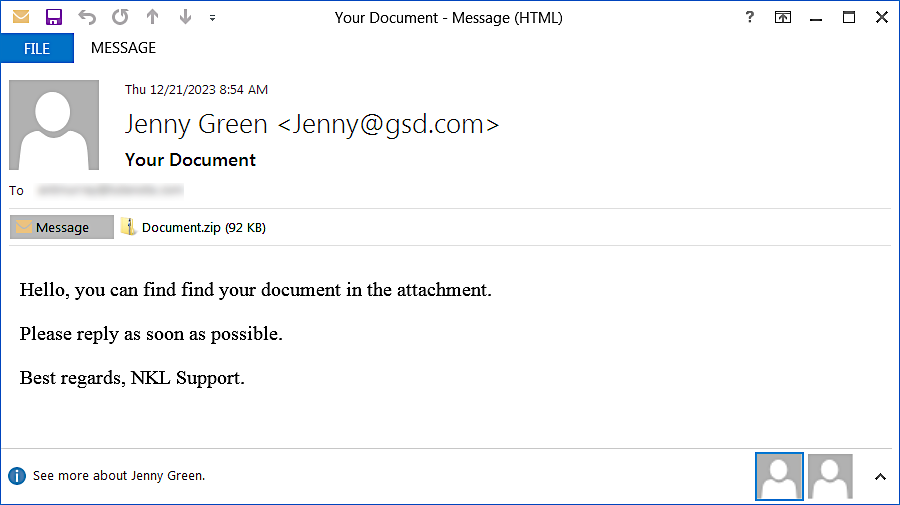
These phishing emails with “your doc” and “photograph of you???” topic strains are being despatched utilizing “Jenny Brown” or “Jenny Inexperienced” aliases from over 1,500 distinctive IP addresses worldwide, together with Kazakhstan, Uzbekistan, Iran, Russia, and China.
The assault chain begins when the recipient opens the malicious ZIP archive attachment and executes the binary inside.
This executable then downloads a LockBit Black ransomware pattern from the infrastructure of the Phorphiex botnet and executes it on the sufferer’s system. After launching it, it can try to steal delicate knowledge, terminate companies, and encrypt recordsdata.
Cybersecurity firm Proofpoint, which has been investigating these spray-and-pray assaults since April 24, stated on Monday that the risk actors goal firms in numerous business verticals worldwide.
Though this method will not be new, the huge variety of emails despatched to ship the malicious payloads and ransomware getting used as a first-stage payload make it stand out regardless that it lacks the sophistication of different cyberattacks.
“Starting April 24, 2024 and persevering with every day for a few week, Proofpoint noticed high-volume campaigns with thousands and thousands of messages facilitated by the Phorpiex botnet and delivering LockBit Black ransomware,” Proofpoint safety researchers stated.
“That is the primary time Proofpoint researchers have noticed samples of LockBit Black ransomware (aka LockBit 3.0) being delivered through Phorphiex in such excessive volumes.”
The Phorpiex botnet (often known as Trik) has been lively for over a decade. It advanced from a worm that unfold through detachable USB storage and Skype or Home windows Dwell Messenger chats into an IRC-controlled trojan that used electronic mail spam supply.
Whereas it slowly grew to an enormous measurement, controlling over 1 million contaminated units after years of exercise and improvement, the botnet’s operators tried promoting the malware’s supply code on a hacking discussion board after shutting down the Phorpiex infrastructure.
The Phorpiex botnet has additionally been used to ship thousands and thousands of sextortion emails (spamming over 30,000 emails per hour) and, extra lately, used a clipboard hijacker module to switch cryptocurrency pockets addresses copied to the Home windows clipboard with attacker-controlled ones.
Inside a yr after including crypto-clipping assist, Phorpiex’s operators hijacked 969 transactions and stole 3.64 Bitcoin ($172,300), 55.87 Ether ($216,000), and $55,000 price of ERC20 tokens.
To defend in opposition to phishing assaults that push ransomware, NJCCIC recommends implementing ransomware threat mitigation methods and utilizing endpoint safety options and electronic mail filtering options (like spam filters) to dam probably malicious messages.
