Safety engineering is a fast-moving discipline with an outsize influence throughout all elements of enterprise—estimates point out that there are trillions of {dollars} at stake. On this ask-me-anything-style Q&A, Toptal safety engineer Gökay Pekşen solutions questions from software program builders world wide, masking main compliance frameworks, high cloud and AWS safety checks, and the significance of DevSecOps within the cloud.
Early in his profession, Gökay turned one among Turkey’s first Licensed Moral Hackers; he later constructed Turkey’s first DevSecOps steady integration and steady supply (CI/CD) pipeline. He’s the founder and CEO of Prime Risk, a cybersecurity consultancy that helps companies navigate GDPR compliance and threat administration, and brings 15 years of expertise in IT safety to this dialog.
Editor’s be aware: Some questions and solutions have been edited for readability and brevity.
Getting Began With DevOps and Safety Engineering
What does a safety engineer do? What sorts of duties do you’re employed on everyday?
—M.D., Seattle, United States
A safety engineer safeguards a company’s digital property and information from cyberthreats. They assess dangers, design and implement safety measures, and implement insurance policies and procedures to make sure the integrity and confidentiality of IT sources. Safety engineers conduct common audits, handle vulnerabilities, and reply to safety incidents, working to stop breaches and mitigate their influence.
My day-to-day work varies drastically relying on what sort of venture I’m engaged on. If it’s an data safety venture, I normally analyze the technique, test the processes, regulate them to the dynamics of the respective firm, and write documentation. If it’s a cybersecurity venture, I normally conduct penetration checks, management the principles and configurations, and implement or enhance safeguards. I like working with firms as a Digital Chief Info Safety Officer (vCISO) as a result of I get pleasure from creating methods and guiding groups on learn how to implement them.
Are you able to inform us extra about learn how to develop into a safety engineer? What was your path into this profession?
—S.S., Minneapolis, United States
Whereas engaged on my bachelor’s diploma in pc engineering, I turned one of many first Licensed Moral Hackers in Turkey. This naturally drove me to develop into a safety skilled. All through my profession, I’ve at all times stayed centered on the basics, notably Linux, networking, and C. I’ve additionally invested time in coaching and mentoring others, which has developed my skilled community and additional superior my very own abilities over time.
To develop into a safety engineer, you might need to pursue increased training in pc science, data expertise, or cybersecurity. Contemplate looking for out internships in one among these fields as effectively. It would take time to develop foundational technical experience with programming languages, working methods, and networking ideas. Familiarize your self with cybersecurity and DevOps fundamentals, together with encryption, entry management, and safety protocols. Past technical abilities, efficient communication and problem-solving abilities are essential for achievement on this discipline.
What path do you counsel for somebody in DevOps and cloud infrastructure to increase their area information into cybersecurity and DevSecOps? Are there books or programs you’d advocate?
—W.Y., Vancouver, Canada
If you’re a newbie, you might begin by pursuing a CEH or OSCP course—however you want extra than simply certifications to hone your experience. Books like Cybersecurity Necessities by Charles J. Brooks et al. can present a complete introduction to cybersecurity fundamentals. These with a DevOps and cloud infrastructure background ought to give attention to cloud safety and should profit from studying Cloud Safety and Privateness by Tim Mather, Subra Kumaraswamy, and Shahid Latif. From there, you possibly can additional discover DevOps safety integrations by studying DevOpsSec by Jim Hen and Securing DevOps by Julien Vehent; each books present perception into this space.
What’s DevSecOps precisely, and the way can organizations simply getting began with it easily incorporate safety into DevOps? For these ranging from scratch, what’s the optimum technique to arrange a security-focused tradition?
—Ok.S., Montreal, Canada
For my part, DevSecOps represents essentially the most important transformation {that a} enterprise can spend money on proper now. Automation is a caretaker: It eliminates the chance of error, and acts independently of the unfavorable elements of human nature. Routines is usually a burden, and guide operations invite too many alternatives for errors or carelessness. Repeating the identical duties could make us inefficient and trigger us to lose focus and curiosity. As human beings we want challenges and new experiences. Who desires to deploy similar machines from a template, run the identical guidelines time and again, or learn supply code till the tip of time? I don’t suppose anybody does.
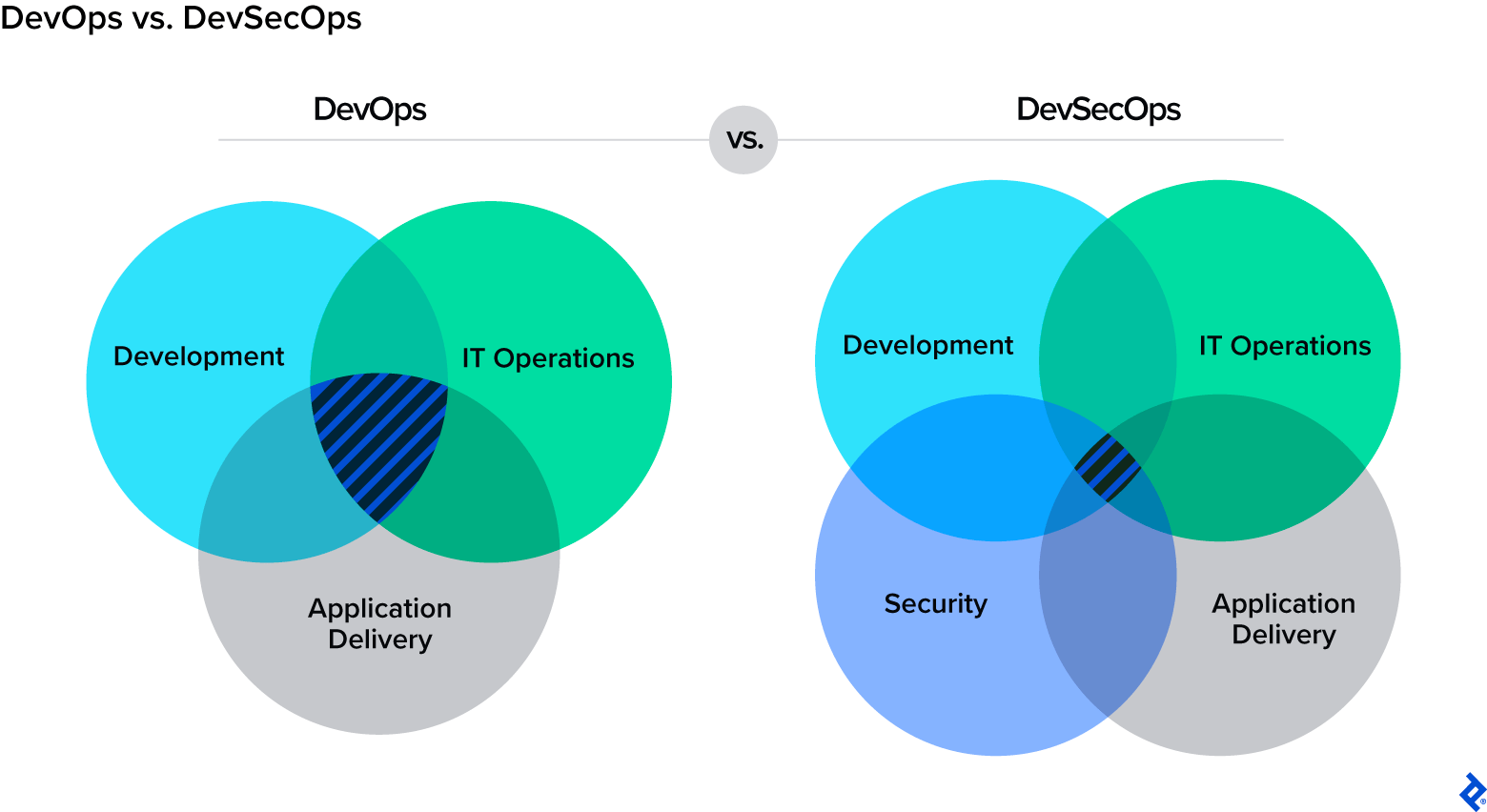
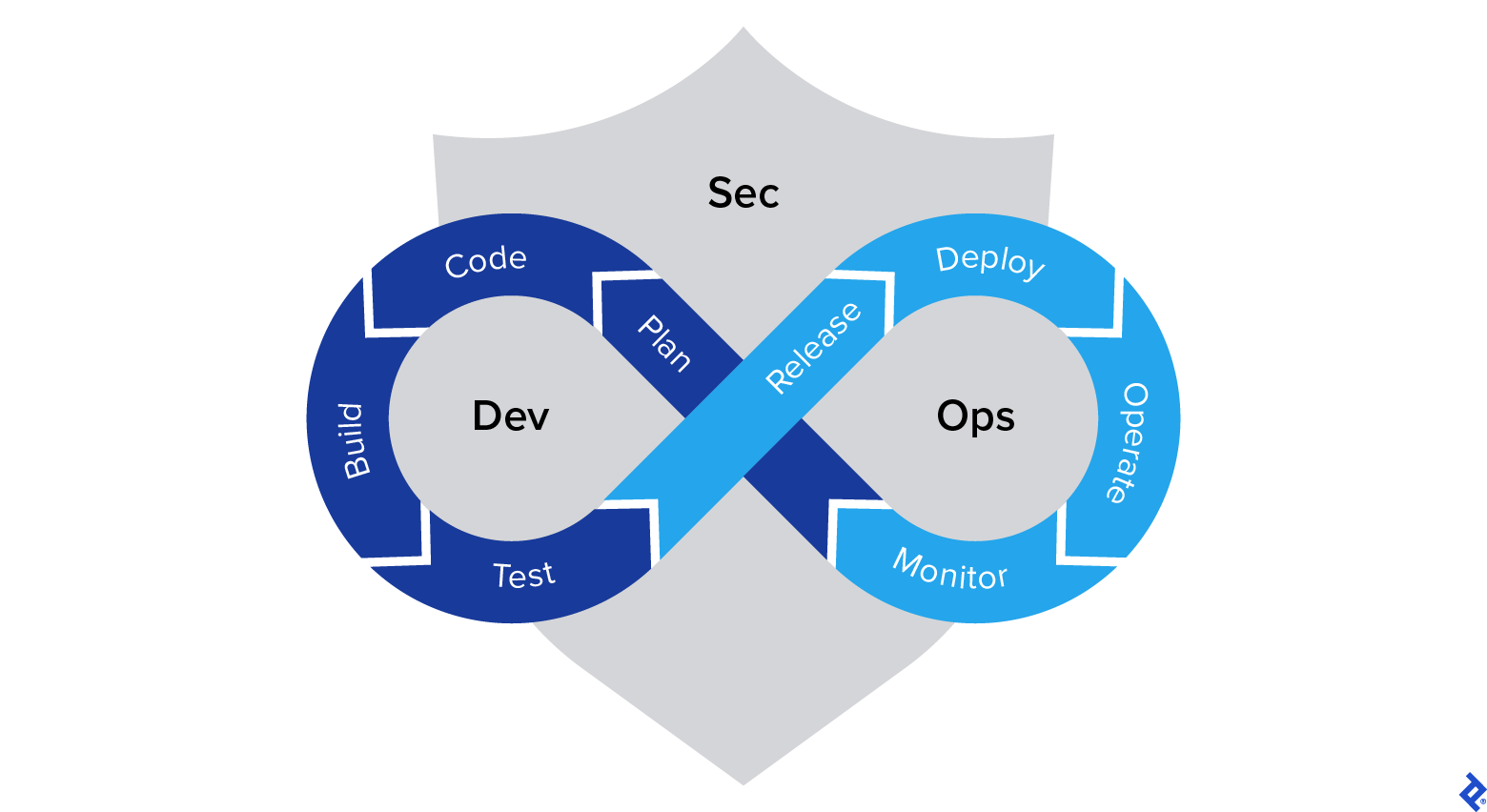
DevSecOps mixes three essential components of IT into one pot: improvement, safety, and IT operations. It’s difficult to collect these large subjects collectively, and it’s even tougher to handle them as one cohesive unit. I’ve carried out or in any other case been concerned in many various CI/CD pipelines, and I’ve noticed firsthand how operations immediately develop into extra environment friendly whenever you remove the burden of guide operations.
Establishing a safety tradition is difficult; in actual fact, I’d say it’s practically inconceivable to domesticate from the within. There might be resistance from workers who could also be set of their methods, and you will want somebody to information you and illuminate the trail. More often than not this implies you’ll require a consultancy to step in.
Safety Concerns and Greatest Practices for Companies
What are the principle variations between main compliance frameworks? Are any notably suited to particular industries?
—Ok.S., Montreal, Canada
Frameworks and requirements are similar when utilized to entities or property, however they differ for industries. Consider it this fashion: A firewall is a firewall—regardless of the place you place it. For those who consider entities by their attributes, they are going to act the identical in each framework. However the goal of the entities or property will differ from business to business. For instance, an online server might deal with monetary information for a banking firm, however it is going to deal with private identifiable data (PII) for a well being establishment: similar entity, completely different sector, completely different outcomes.
ISO 27001 is the commonest normal for safety. A lot of the requirements and frameworks are constructed on ISO 27001, in order that’s the perfect place to start out, whatever the business. Making use of it to your each day job is the simplest technique to know it.
What primary safety checks would you advocate to check an online software?
—Ok.G., Łódź, Poland
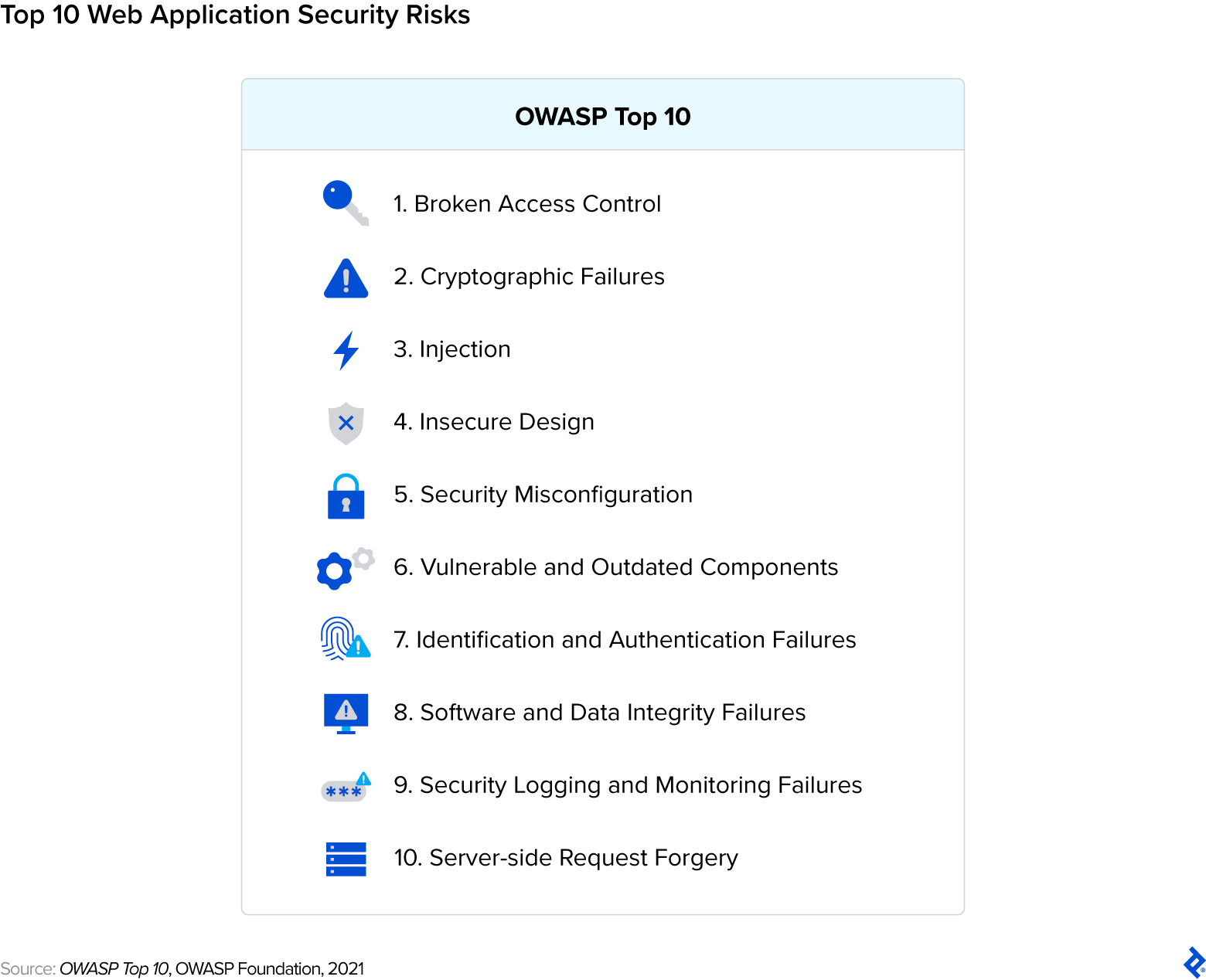
The highest 10 listing from the Open Internet Software Safety Mission (OWASP) is a should for net software safety; I like to recommend it to everybody. It’s a set of standardized and developer-friendly sources to assist organizations establish, prioritize, and mitigate essentially the most important safety vulnerabilities in net purposes. It’s additionally up to date frequently.
With so many various AWS choices, the place ought to groups get began with regard to AWS safety finest practices? What are essentially the most important providers to safe?
—Ok.S., Montreal, Canada
The reply to this query largely depends upon what providers you’re utilizing. AWS is an enormous world; there are such a lot of completely different instruments and providers at each stage of the tech stack. Establish and entry administration (IAM), net software firewall (WAF), digital personal cloud (VPC), CloudTrail, S3 bucket safety, and infrastructure as code (IaC) instruments are all nice locations to start out, and relevant to most AWS customers working at scale. There are further instruments obtainable for information safety and automation that you could be need to look into, relying in your particular use case. I’d advocate consulting with an AWS specialist to find out your wants.
The Way forward for Cybersecurity
Might you define the influence of the advances in generative AI in your work?
—J.B., Vienna, Austria
I create the best way, and generative AI walks the trail. I inform it to create distinctive documentation units to adjust to particular frameworks for the businesses. I ask it to test code to see whether it is susceptible to any exploits or to find out whether or not a configuration file might result in a cybersecurity assault.
Generative AI seems like an entire new frontier on this discipline. I exploit it each day. It’s particularly useful after I have to shortly discover ways to use new instruments and applied sciences.
What are the challenges when implementing zero belief structure (ZTA) in cloud-based environments?
—O.T., Istanbul, Turkey
Zero belief places the precept of “by no means belief, at all times confirm” into motion, as a response to the extra conventional strategy of “implicit belief,” by which customers and their units are assumed to be reliable after they’re verified and related to a permissioned community. ZTA is about privilege administration: It goals to stop malicious actors from shifting laterally by means of the community to achieve delicate supplies to which they weren’t explicitly granted entry.
Nonetheless, ZTA is a generally misunderstood matter as a result of safety distributors are more and more remarketing their merchandise to capitalize on the novelty of this time period, even when it won’t be related or relevant. They usually describe any firewall, endpoint safety platform, or entry administration software (like IAM) as performing like ZTA—however this isn’t technically true. Merely making use of a safety product to a community is a a lot completely different expertise than sustaining a tradition of safety inside that community; no particular person product can change the continued work required to place ZTA into follow.
Earlier than you implement ZTA, you have to take all related stakeholder, shareholder, provider, and connection relationships into severe consideration. The cloud is supposed to be a extra versatile and free setting than what we work with in enterprise software program. To make {that a} actuality, firms have to be meticulous about figuring out what’s actually essential to safeguard. Defending confidential data is not only an moral obligation—it’s additionally good for enterprise. By securing your financial engine, you construct belief and preserve a aggressive edge.
How do you suppose exploits will proceed to evolve? Initially we had binary injections, net exploitation, SQL injection, and HTTP compromise—to not point out good old school social engineering, like phishing. What’s subsequent? What’s the most recent development?
—J.O., Fortaleza, Brazil
Generative AI is simply now starting to point out us distinctive exploits and payloads which have by no means been seen earlier than. It really works in opposition to us. Earlier than lengthy, we’ll begin to see completely different assault strategies and exploits due to the brand new vectors created by AI. I want I might say extra about this, however it will be harmful to share too many particulars.
Going ahead, each new assault will evolve and alter itself by gathering and responding to data in its setting. We’re additionally starting to see assaults on AI-based operations, like information poisoning within the generative AI ecosystem. Issues will change. Safety professionals are already devising immediate firewalls to stop ChatGPT information leakage.
The following massive factor might be quantum safety, however it could be too quickly to debate it. Quantum safety is an interdisciplinary discipline that mixes elements of quantum physics, arithmetic, and pc science, and opens up alternatives for collaboration throughout these domains. Ahead-thinking organizations, particularly these with long-term information safety wants, are exploring and adopting quantum-resistant encryption options to future-proof their information safety.
Nonetheless, it’s important to notice that whereas quantum safety is gaining momentum, it could solely partially change conventional encryption in some use instances. Some cryptographic algorithms are computationally safe even in opposition to quantum assaults, and never all information requires quantum-resistant encryption.
The editorial staff of the Toptal Engineering Weblog extends its gratitude to Aditya Krishnakumar for reviewing the technical content material offered on this article.